


WHITE PAPER
1 September 1997
Army CI/HUMINT XXI Concept of Operations:
"Providing a Seamless LinkageóStrategic to Tactical"
Recommendations for a single, versatile Counterintelligence and Human Intelligence force ---
reorganized to concentrate capabilities where they are required,
redefined military occupational specialties for enlisted soldiers and warrant officers,
re-equipped to assure synchronized national to mud operations across the spectrum of conflict.
PREFACE
CONTINUITY WITH THE PAST. In this White Paper, we maintain continuity with the enduring challenges of Counterintelligence (CI) and Human Intelligence (HUMINT), which include the use of IPW, ASAS, SOF, and Long Range Surveillance Units. As in the past, CI in Force XXI must detect, identify, exploit and neutralize adversary efforts to gain information, exploit our vulnerabilities, and strike our organizations and facilities. HUMINT will continue to derive information collected from and provided by human sources that penetrate an adversaryís decision making architecture for data regarding capabilities (strength and weaknesses), vulnerabilities, dispositions, plans and intentions. While the world has changed dramatically and technological advances are enabling major changes in the military, CI and HUMINT in some respects remain unchanged. The target (human being) and the sensor (human being) remain constant. Technological advances enable our future CI and HUMINT to better execute and support execution of the five core functions: See, Shape, Shield, Strike, and Move.
CHANGE FOR THE FUTURE. In this White Paper, we recognize the need for future change and address those needs. We envision a CI and HUMINT force that will better enable a Commander to SEE the battlespace. CI and HUMINT are inherent to achieving situational understanding by assuring that Commanders and senior decision makers SEE enemy forces, friendly forces, neutral elements and the environment. The future CI and HUMINT force is integral to Information Operations that SHAPE the battlespace assuring that friendly forces are in a position of strength while the adversary operates from a position of weakness. CI and HUMINT activities will provide the necessary information to SHAPE neutral elementsí positions toward friendly operations and activities. CI and HUMINT will conduct the full array of active and passive operations designed to SHIELD friendly organizations, installations, and operations from adversary activities. CI and HUMINT efforts will provide the information required by a Commander and senior decision makers to preserve combat power and operational freedom by protecting the force and assuring operational security. CI and HUMINT will provide information required for the precise application of friendly STRIKEs. In addition, Commanders and senior decision makers may use CI and HUMINT resources to conduct nonlethal strikes at decisive points to deter hostile action, impose order, protect the force, or compel an adversary or ally to do our will. Our future CI and HUMINT force will have the agility to MOVE with the maneuver force and respond to national requirements. Advanced technology will allow CI and HUMINT information to MOVE rapidly to match the tempo and speed required for successful maneuver operations. CI and HUMINT will contribute to Commander and senior decision maker resolve to position forces for immediate and follow-on operations.
GROWTH. While the CI and HUMINT force will not grow, mission sets and customers are growing. The dramatic geopolitical changes resulting from the end of the Cold War produced a plethora of potential adversaries, traditional and nontraditional. While the past allowed CI and HUMINT forces to concentrate on a single set of targets, the future requires an agile force that can shift between multiple target sets and respond to requirements from national decision makers to tactical commanders. The evolution of Information Operations creates new requirements and opportunities for CI and HUMINT products and activities. Commanderís may use CI and HUMINT resources in an Information Operation to achieve an asymmetric advantage over an adversary contributing to Information Dominance. CI and HUMINT will leverage new technologies to assure efficient and effective accomplishment of mission sets for all customers.
FUTURE. We will organize, train, and equip the future CI and HUMINT force to answer requirements at each echelon. The force will include a mixture of active component and reserve component soldiers. We envision a force that is interoperable with other services and national agencies. We require a force that includes not only the traditional CI and HUMINT organizations but also the capability embedded in Long Range Surveillance and Special Operation Forces. We believe each echelon will sustain skills unique to their requirements and an ability to surge resources up or down. In the tactical echelons, CI and HUMINT will concentrate on collection and analysis functions with a focus on commanderís priority intelligence requirements. At the tactical level, all soldiers will routinely perform CI and HUMINT tasks and must have the skills to shift from one set of functions to the other based on the needs of the commander. At the operational level, the force will conduct investigations, surveillance operations, Long Range surveillance Operations, and all source analysis to satisfy Army Component Commander, Joint Land Force Component Commander, and Joint Commanderís priority intelligence requirements. Operational level soldiers must have the skills to shift between CI and HUMINT, but will focus on one set of functions. At the strategic and departmental level, the Army will execute the full spectrum of counterintelligence functions to satisfy senior decision maker and statutory requirements. The strategic and departmental force will focus on executing the most sensitive investigations, operations, and collection efforts, assuring an all source production activity. While some HUMINT functions may be executed by strategic and departmental level soldiers, human intelligence functions will remain concentrated in the Defense HUMINT Service.
SUMMARY. Throughout our Armyís 222 years, soldiers and civilians performed counterintelligence and human intelligence functions. From catching the first significant espionage agent (Benedict Arnold) and the conduct of espionage (Nathan Hale) to their modern day counterpart and into the 21st century, our Army requires dedicated, well trained, superbly equipped soldiers and civilians to maintain continuity with past while changing for the future. Force XXI and the Army After Next requires an information age CI and HUMINT force that leverages modern technology to satisfy century old requirements. CI and HUMINT are in a growth market and this White Paper endeavors to position our forces for the 21st century and beyond.
1. Purpose.
a. The document reflects the re-engineering recommendations of the CI/HUMINT Integrated Concept Team, 23 January 1997, as modified by the CI/HUMINT Council of Colonels on 12 February 1997.
b. The purpose of this paper is to outline Integrated Concept Team (ICT) and Council of Colonels recommendations regarding the future operational requirements of US Army Counterintelligence (CI) and Human Intelligence (HUMINT) through Army XXI (2010). TRADOC Pamphlet 525-5, Force XXI, outlines the Armyís future warfighting requirements; TRADOC Pamphlet 525-75, Intelligence XXI, details what the Army intelligence community must do to meet these future requirements. Technological advances, diverse threats, changing operating environments, force reductions, and concomitant expanding commander needs demand that we act now. This CONOPS captures lessons learned from recent operations and exercises, field initiatives, and experimentation findings. It represents our best estimate of future CI/HUMINT warfighting requirements and translates into what we term "Army CI/HUMINT XXI."
c. The CONOP recognizes those requirements identified in regulatory and policy documents dating back to the National Security Act of 1947, e.g., Titles 10, 18 & 50 United States Code; Executive Order 12333; DoD Directives and Army Regulations. Where there is an appearance of conflict, regulatory and policy documents take precedence.
d. This CONOPS does not address all aspects of Human Intelligence, particularly the means by which we will integrate combat support and service support observations, information gained from tactical patrols, and Long-range Surveillance reporting. We briefly address LRS/SOF reporting and communications requirements, but intentionally deferred discussion of other Human Intelligence sources to better narrow the scope of our CI/HUMINT re-engineering task.
2. Summary. Our primary focus in this effort was to bring CI/HUMINT into the mainstream of digitized, intelligence operations consistent with Force XXI patterns of operations. We did not strive to re-engineer the ancient tradecraft of CI/HUMINT; we worked to define means by which we may better posture and equip our traditional CI/HUMINT forces for the future battlefield.
a. Future commanders will fight simultaneous, distributed, non-linear operations against enemies ranging from conventional to criminal, and will demand an immediate, all-source intelligence product tailored to their needs. CI/HUMINT will play an important role in building this all-source product and will prove particularly critical in three of the six patterns of operation.
(1) Protect the Force. CI/HUMINT will support force protection from the sustaining base to the objective area through inter-echelon collection and reporting. Similarly organized, equipped, trained, CI/HUMINT teams from strategic to tactical can surge to occupy those areas most threatening to our operations.
(2) Shape the Battlespace. CI/HUMINT reporting is our best source for determining threat intentions and plays an important targeting role with respect to threat personalities, intelligence systems, and organizations. Whether in a Major Regional Conflict or Stability and Support Operation, CI/HUMINT reporting will allow the commander to precisely identify, locate, track, and attack elements comprising the threat or "situation" center of gravity and, accordingly, shape his battlespace in preparation for decisive operations.
(3) Gain Information Dominance. Knowledge is power. Gaining information dominance means gaining and maintaining an information edge relative to the enemy. CI/HUMINT contributions to this pattern are threefold: first, CI/HUMINT reporting complements reporting from other disciplines, giving the commander the reliable all-source picture he needs to prosecute the battle quickly and precisely; second, CI/HUMINT identifies those elements critical to threat information processing and the means by which the commander can deceive, degrade, or deny these capabilities (C2 Attack); and third, by contrasting friendly operations against threat collection capabilities, CI/HUMINT identifies those areas in which friendly forces are most vulnerable and those measures commanders can take to defend against threat intrusions (C2 Protect).
b. Our Concept of Operations envisions an internetted CI/HUMINT force from strategic to tactical, similarly organized, trained, and equipped to afford maximum flexibility during conflict. We recommend standardizing the CI/HUMINT structure across the echelons, an effort requiring the consolidation of CI/HUMINT DS companies resources(less a small two-person planning cell) at the MI Battalion GS Company. These changes promise training efficiencies and better posture our teams for flexible surge operations. We further concluded that we have four major CI/HUMINT functions: investigations, operations, collection and analysis. We further concluded that the tactical force focuses on collection and analysis while operational and strategic forces perform all the functions. We recommend combining CI Agent and Interrogator specialties to form a single specialty and, recommend merging MDCI Analyst responsibilities with those of the all-source Intelligence Analyst and divesting COMSEC monitoring functions altogether. Finally, we recommend establishing and fielding a common equipment baseline--enabling teams at all echelons to rapidly process and pass reports, collaborate in planning, and seamlessly reinforce during contingencies.
3. Background
a. Operational and tactical level Army CI and HUMINT have undergone significant changes over the past several years. US military operations in Grenada, Panama, Somalia, Bosnia, and during DESERT STORM demonstrated the need for precise, timely CI/HUMINT support, fueling efforts to better organize the entire CI/HUMINT force for diverse operational and tactical operations.
b. Strategic Army HUMINT was merged with other services strategic HUMINT in the establishment of the Defense HUMINT Service (DHS) in October 1995, a joint agency which assumed control of Army and other service strategic HUMINT resources. This action gained certain efficiencies at the strategic level, but it placed additional stress on operational and tactical CI/HUMINT, particularly with respect to the management of joint interrogation facilities and debriefing centers, and the conduct of tactical source operations.
c. While providing unique expertise and a reinforcing capability to the operational and tactical force, strategic level counterintelligence activities remains essentially unchanged. The enduring strategic counterintelligence challenge remains the identification and neutralization of espionage activities. The Armyís responsibilities in meeting this challenge is set forth in regulatory and policy documents.
d. Responding to a requirement to plan the future for Army counterintelligence and human intelligence, senior military intelligence leaders chartered and subsequently approved a "CI/HUMINT Action Plan" on 1 March 1996. A joint USAIC&FH, DA DCSINT, and INSCOM effort, the Plan identified actions, milestones, and action leads for every major aspect of CI/HUMINT operations.
e. TRADOCís Requirement Determination process made its debut in June 1996. Representing a radical change in how the Army identifies and resources future requirements, this new policy directed that proponent-established Integrated Concept Teams (ICT) define all future requirements and that requirements not validated during an ICT process will remain unfunded by the Army. The ICT process seeks to leverage requirements and funding generated outside the Army, e.g., the Defense Counterintelligence Requirements Panel.
f. Using the CI/HUMINT Action Plan as a starting point, USAIC&FH commissioned the CI/HUMINT ICT in July 1996. This CONOPS represents the ICTís key judgments and recommendations for building, employing, and equipping Army CI/HUMINT XXI. We have modified this CONOPS to conform to Council of Colonel recommendations levied on 12 February 1997.
g. In the following sections, we present the argument for a reengineered Army CI/HUMINT force. To establish CI/HUMINTís place on the future battlefield, we first briefly outline mission, roles, and functions. We follow this discussion with an assessment of the current problem and a concept of operations (CONOPS) we believe is our best solution. We follow the CONOPS with a delineation of CI/HUMINT requirements. And finally, we outline some of the DTLOMS implications we see and conclude with a brief summary. These basic sections reflect our most important considerations and recommendations. Follow-on appendices contain detailed information and analysis of use to doctrine, force structure, and materiel planners.
4. Army CI/HUMINT XXI Mission, Roles, and Functions. CI/HUMINT brings time-proven, "human-based" collection, exploitation, and analysis capabilities to enhance our ability to focus forces at the right time and place. For example, using the combat power formula delineated by FM 100-5, Operations,:
Combat Power = Leadership (Firepower + Maneuver + Protection)
we clearly can highlight CI/HUMINTís contribution toward Leadership (information detailing battlespace conditions), Firepower (discrete human or adversary infrastructure targets), Maneuver (friendly positional advantages against human targets), and Protection (measures friendly force can implement to shield against or shape the adversaryís view of friendly operations). We believe CI/HUMINTís contribution to combat power will extend through Army XXI virtually intact, and supports the following mission statement and delineation of roles and functions for:
CI/HUMINT Mission Statement
Define, plan, and implement collection, exploitation and analysis strategies in support of requirements across the spectrum of conflict; pay particular attention to adversary strengths, vulnerabilities, capabilities, and intentions; environmental factors, to include those cultural and human influences impacting friendly and adversary capabilities; proactively gather information and conduct activities to protect against espionage, other intelligence activities, sabotage or assassinations conducted by or on behalf of adversaryís including transnational and terrorist organizations; identify, detect, track, exploit, and neutralize adversary efforts to gain information detailing friendly force strength, dispositions, plans, and intentions.
Table 1
CI/HUMINT Roles and Functions
|
Army XXI |
Roles |
Functions
|
|
Counterintelligence |
1. Identify adversary information collection and processing capabilities and vulnerabilities. 2. Identify friendly vulnerabilities to adversary collection efforts. 3. Understand how the adversary processes and disseminates information and intelligence to support their decision making process. 4. Support efforts to influence adversary decisions through support to targeting, deception, PSYOP and OPSEC. |
1. Conduct collection efforts targeting adversary intelligence activities. 2. Plan and execute operations to exploit adversary intelligence activities and support C2 attack. 3. Conduct investigations to prove, disprove, and neutralize indications of espionage, subversion, and other national security crimes by adversary intelligence activities; and support C2 protect. 4. Perform analysis to provide the commander with timely, accurate, and relevant intelligence regarding adversary intelligence activities and predict adversary intelligence actions and reactions.
|
|
Human Intelligence |
1. Collect and report information obtained from human sources and foreign media. 2. Conduct direct collection activities in the area of operations and interest. 3. Provide linguistic support. 4. Provide information on adversary plans, capabilities and intentions. |
1. Interrogate prisoners of war and civilian detainees. 2. Debrief line crossers, refugees and/or émigrés. 3. Translate and report information obtained from foreign documents and media. 4. Debrief Army personnel (military and civilian) for intelligence. 5. Conduct human reconnaissance and surveillance. |
|
Common CI/HUMINT |
1. Participate in the intelligence mission analysis and planning process. 2. Participate in the collection management process. 3. Collect, analyze, disseminate and present CI/HUMINT information and intelligence to support the six intelligence functions. 4. Plan and execute CI/HUMINT activities consistent with the FORCE XXI seven patterns of operation. |
1. Conduct CI/HUMINT Preparation of the Battlespace. 2. Conduct CI/HUMINT specific requirements, mission, and asset management. 3. Conduct CI/HUMINT source operations and other collection activities. 4. Fuse CI/HUMINT reporting for detailed analysis, data basing, cross cueing, and refining collection efforts. 5. Conduct detailed quality control of CI/HUMINT activities and reporting. 6. Predict what the threat views as friendly High Payoff and High Value Targets (HPT/HVT). |
5. The Problem. While Force XXI operating patterns increasingly demand simultaneity, distributed operations, unprecedented precision and timeliness, Army CI/HUMINT largely remains layered, detached, and slow. CI/HUMINT supports the commander and senior decision makers, and must adjust according to their future circumstances. Meeting Army XXI requirements means building the CI/HUMINT force to perform integrated "tactical to strategic" operations consistent with an operations tempo unprecedented in modern military affairs. The strategic counterintelligence force is constantly and fully engaged. Regulatory and policy requirements challenge the strategic forceís ability to achieve necessary agility. We need a strategic force agile enough to shift from peacetime strategic activities to focus on operational and tactical requirements in a time of crisis or conflict. We need an "equi-talented" CI/HUMINT force capable of surging support between operational and tactical levels in both war and stability and support operations (SASO). We need a force with immediate access to the requirements, equipped with the automation tools necessary for conducting rapid analysis, dynamic cross-cueing, and immediate reporting. We need an Army XXI force, supported by Army XXI tools and architectures.
6. The Solution: The concept for Army CI/HUMINT XXI envisions seamless, complementary connectivity between tactical, operational, and strategic echelons, in both peace and conflict. Each echelon has its own unique requirements, yet no one echelon can meet inter-related CI/HUMINT peacetime and battlefield requirements in their entirety. Future CI/HUMINT operations will be effective to the degree that they share common terms, procedures, and architectures, and can effect transparent shifts in scope and focus toward our most critical conflict objectives.
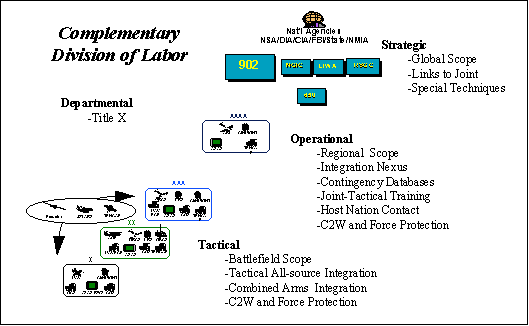
a. Operations in Peace. We envision a dynamic, complementary division of labor during peacetime, posturing the Army CI/HUMINT XXI force for conflict.
(1) Strategic CI. Though our strategic forces consist entirely of CI that is constantly and fully engaged, the close association of CI and HUMINT ensures that this echelon will maintain close contact with HUMINT counterparts within DHS. Consequently, this echelon serves as an essential link between operational/tactical CI/HUMINT and other departmental and national CI/HUMINT agencies, and an indispensable resource for operational and tactical elements in their preparations for conflict. Army strategic CI, in general, plans and executes the full range of CI functions to satisfy regulatory and policy requirements --- plans, coordinates and executes counterespionage activities IAW the National Security Act of 1957, other existing laws, Executive Order 12333, DoD directives and Army Regulations; acts as the Army CI executive agent for treaty verification, DoD acquisition systems protection programs, and all Army special access programs (SAP); shares CI responsibility with Special Operations Forces CI/HUMINT personnel in the protection of SOF elements in CONUS and abroad; and reinforces operational and tactical CI/HUMINT efforts with special techniques, unique technical capabilities, global CI/HUMINT analysis, and CI database maintenance. In the future, the strategic force must achieve a level of agility and capability that allows satisfaction of requirements levied by senior decision makers, laws enacted by Congress and directives in policy documents yet shift from peacetime activities to focus on operational and tactical requirements in a time of crisis or conflict.
(2) Operational CI/HUMINT. Operational CI/HUMINT forces focus on the specific peacetime requirements of the Unified Commander(s), consistent with their designated support relationships. These relationships can range from direct support to operational control and typically are in response to unique geographical requirements and/or contingency missions. Operational CI/HUMINT draws from strategic resources in meeting theater commander-in-chief (CINC) requirements, and coordinates with subordinate tactical CI/HUMINT elements to better posture the theater CI/HUMINT force for conflict. In general, operational CI/HUMINT focuses on specific regional adversaries to detect changes in adversary intelligence plans or intents; develops and maintains detailed CI/HUMINT order of battle, including cultural, political, and other constraints relative to enemy capabilities or the potential friendly mission; identifies, locates, and tracks adversary elements capable of threatening friendly forces during forced-entry or follow-on operations; and conducts detailed investigations regarding adversary efforts to gain information on friendly forces, as required. The agility challenge for operational CI/HUMINT forces is to shift from peacetime activities throughout a Unified Commanderís area of responsibility (AOR) to focus on a specific crisis while maintaining a AOR-wide overwatch capability.
(3) Tactical CI/HUMINT. Tactical CI/HUMINT forces build and maintain habitual support relationships with combat forces, exercising this relationship through all forms of combined arms training. These forces work closely with their operational counterparts to establish complementary training goals, adversary data bases, database maintenance responsibilities, and investigations, as required. General Tactical CI/HUMINT requirements include ensuring realistic CI/HUMINT training as part of combined arms operations; keeping the supported commander informed of adversary plans and intents against friendly forces, as well as measures the commander can take to minimize vulnerabilities; coordinating with the Analysis Control Element and other tactical intelligence agencies to effect timely contributions to the all-source picture; and conducting investigations on behalf of the commander in coordination with operational or strategic CI/HUMINT agencies. The agility challenge for tactical CI/HUMINT is to shift from a training and readiness environment that does not routinely challenge all CI/HUMINT soldiersí skills to high OPTEMPO operations directed at specific adversary.
b. Operations in Conflict. The Army CI/HUMINT XXI force will meet Army information requirements in the sustaining base, sanctuary, and forward areas in both war and SASO. Early entry of CI/HUMINT forces and timely CI/HUMINT preparation of the battlefield are essential as combat units transition from peace to conflict. Connectivity with warfighting commanders will be continuous and dynamic--from planning and deployment, through force build-up, decisive operations, and redeployment. Versatile and integrated, the combined force will adjust its focus and resources according to the situation and evolving requirements, with the CI/HUMINT echelon closest to the warfighting commander acting as the integration or synchronization headquarters.
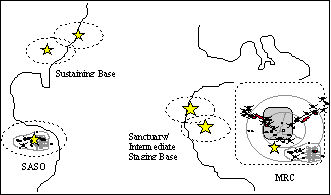
(1) Strategic CI. In most instances, Army Strategic CI will support the warfighting commander with specific resources and by internally adjusting its priority of effort. However, regulatory and policy requirements will not disappear with the deployment of combat forces. Counterespionage activities, support to sustaining base organizations, and satisfaction of requirements not related to the current crisis will continue. With increased agility, the Strategic CI force will support the warfighting commander with efforts conducted in sanctuary and by reinforcing operational and tactical CI/HUMINT elements with information support, tangible resources, or both, consistent with the particular needs of the operational environment.
(2) Operational CI/HUMINT. Operational CI/HUMINT forces support the warfighting commander in all phases of the deployment, ensuring adequate CI/HUMINT support from the sustaining base to the objective area. Ideally forward prior to the entry of combat forces, operational CI/HUMINT elements translate commander requirements into tangible CI/HUMINT tasks, fulfill these tasks using organic resources, and, as required, coordinate and/or request additional support from strategic and tactical CI/HUMINT elements. CI/HUMINT responsibilities fulfilled at this echelon include coordinating all supporting CI/HUMINT actions to ensure unity of effort; coordinating, establishing, and/or maintaining collection and exploitation operations in theater to include source operations, joint debriefing centers, joint interrogation facilities, and liaison with host-nation security service or law enforcement agencies; and supporting the commander with Command and Control Warfare (C2W) products such as assessments, estimates, and specific threat analyses. The Operational CI/HUMINT forceís organic connectivity and agile transition from peace to conflict assures timely, precise, distributed and simultaneous operations to satisfy requirements.
(3) Tactical CI/HUMINT. Tactical CI/HUMINT forces conduct collection and analysis functions consistent with their commanderís intent and the CI/HUMINT battlefield shaped by operational CI/HUMINT efforts. Tactical CI/HUMINT leverages strategic and operational forces by focusing their unique capabilities and databases to answer the requirements of the commander in contact. Tactical CI/HUMINT can play a supporting role in manning joint facilities and centers, but will likely remain with tactical combat forces to support mission planning and execution. Specific Tactical CI/HUMINT responsibilities include ensuring integrated CI/HUMINT support to the immediate tactical commander; conducting collection and exploitation operations promising immediate tactical value; and complementing operational CI/HUMINT collection and exploitation efforts within their area of operations to include source debriefings, EPW interrogations, liaison with select local officials, and security investigations, as required.
c. The above CONOPS narrative captures the essence of what we envision for the Army CI/HUMINT XXI force. Integrated, complementary, versatile, focused, agile -- the CONOPS supposes a CI/HUMINT force organized, equipped, and trained to support warfighting commanders and senior decision makers by executing Intelligence XXI tasks across the six Force XXI patterns of operations. We examine CI/HUMINT contributions toward satisfying "patterns of operations" requirements in Appendix 1. Appendix 2 details how we view CI/HUMINTís execution of Intelligence XXI tasks.
7. Requirements Delineation. Requirements stem from statutory responsibilities and those future operational capabilities CI/HUMINT must possess to support the warfighting commander and senior decision makers. The Army CI/HUMINT XXI mission, roles, and functions discussion highlighted what CI/HUMINT brings to the warfighterís table. The CONOPS details how we envision synchronizing CI/HUMINT echelon contributions. Listed below are the general requirements Army CI/HUMINT XXI must have satisfied in order to meet its mission, roles, and functions, according to the CONOPS. We detail specific requirements for each echelon in Appendix 3.
Table 2
General CI/HUMINT Requirements
|
1. Definition of common terms, procedures, and products from national to tactical. 2. Identification of tasks, conditions, and standards common to each echelon and the incorporation of task training at institutional, unit, and individual levels. 3. Automated connectivity to the All-Source Analysis System and joint CI/HUMINT unique processors allowing rapid, push-pull access to intra-echelon CI/HUMINT databases and access to the all-source picture of the battlefield. 4. Near-real-time voice, data, and video communications between echelons and the supported commander. 5. Standard message and reporting formats interoperable from national to tactical IAW common operating environment standards. 6. Automated analysis tools supporting link and association analysis. 7. Automated collection management tools supporting rapid identification of CI/HUMINT collection gaps, available resources, and dynamic cross-cueing both within and across echelons. 8. Standard mission, requirements, and asset management protocols between echelons. |
8. CI/HUMINT CONOPS Impact By DTLOMS. Meeting Army CI/HUMINT XXI requirements will require substantial adjustments within each of the DTLOMS categories. This section highlights what we believe to be the most significant adjustments. We provide a more detailed impact analysis at Appendix 4.
a. Doctrine. Implementing this CONOPS requires harmony with the National Security Act of 1947, United States Code, DoD Policy, Joint doctrine Army regulations and Army doctrine. With respect to Army requirements, we anticipate modification of existing Army regulations and significant revisions to numerous Field Manuals including FM 34-1 (Intelligence and IEW Operations); FM 34-2 (Collection Management and IEW Synchronization); FM 34-5(S)(HUMINT Operations); FM 34-52 (Interrogation); FM 7-93 (Long Range Surveillance Unit OPERATIONS); FM 100-25 (ARSOF Operations) and FM 34-60 (Counterintelligence).
b. Training. An "equi-talented" Army CI/HUMINT force must possess a common core of individual and collective tasks, and the opportunity to exercise them in field exercises and simulations. We see the requirement for identification of these common core tasks, integration of CI/HUMINT into joint, CTC, and unit exercises, and the development of a robust simulation capability for use both in garrison and in the field. Training at all echelons must focus on creating a CI/HUMINT force agile enough to shift from peacetime activities to conflict resolution.
c. Leadership Development. Maximizing CI/HUMINT contributions means understanding how to leverage their capabilities amidst competing requirements and risks. For example, Force Protection concerns often compel commanders to constrain CI/HUMINT team and unit movements, yet constraining those unit activities denies the commander relevant Army CI/HUMINT reporting and contributes to an intelligence fog--one conceivably making his larger force vulnerable to harassment and attack. On another note, Commanders are responsible for all actions in their areas of operation, yet today the CI/HUMINT landscape often includes operations outside the purview of the responsible senior intelligence officer. In the future, Commanders must insist that their senior intelligence officer is knowledgeable of such operations. Each agency brings unique capabilities and focus to the CI/HUMINT effort. Commanders and intelligence leaders need to understand these agencies in order to leverage their capabilities and limitations consistent with battlespace requirements and commander intent. The Commander Drives Intelligence--he alone calculates risks and synchronizes operations in his battlespace. We need to ensure current and future commanders comprehend their critical role in CI/HUMINT operations. We believe that the program of instruction at all Combat Arms Officer Advanced Courses should be reviewed to assure coverage of CI/HUMINT operations early in future leaders professional development. Concurrently, we believe "Leveraging CI/HUMINT Capabilities" should be addressed at all intelligence NCO and officer professional development courses, as well as during Pre-Command Courses. Ultimately, it is the influence of the intelligence officer on the commander that assures proper utilization of resources.
d. Organization. Surging CI/HUMINT support between the echelons requires substantial command and control capabilities and creation of an agile CI/HUMINT force. Such agility occurs in organizations that successfully execute CI/HUMINT functions on a daily basis. We believe we should carefully examine the current structure and location of our CI/HUMINT force with an eye toward ensuring our future force can respond quickly and adequately to the contingencies addressed in the Joint Strategic Capabilities Plan (JSCP). In addition, we recommend consolidating and standardizing CI/HUMINT team structures at each echelon, an action requiring the consolidation of Division CI/HUMINT assets at the MI Battalion GS Company.
e. Materiel. We cannot achieve dynamic, inter/intra-echelon connectivity without substantial materiel improvement. We see the need for common hardware assuring access to all-source products, intra-echelon databases, and the CI/HUMINT operators common to each. We need robust voice, data, and video communications linking agents to agents, echelons to echelons, and CI/HUMINT elements to commanders; as well as collection, investigative and analysis tools - automated voice translators, source reliability detectors, long-range listening devices, retinal scanners, and advanced association software.
f. Soldiers. The Army CI/HUMINT XXI soldier will be versatile in all major aspects of CI/HUMINT operations. Our current force structure caveats soldier skills according to three military occupational specialties and two warrant officer/officer fields. We recommend combining MOSs 97E and 97B into a single CI/HUMINT specialty, and redesigning most 97G Analyst positions as 96B Intelligence Analyst billets. We also recommend combining warrant officer specialties, 351B and 351E, into a single 351X MOS. We also recommend the creation of a certification program that begins as a Novice with graduation from IET that transitions to Journeyman as a senior E-6 or acceptance as a Warrant Officer and becomes a Master Operator as an E8 or senior CW3. Individuals will receive the certification only after completion of specific training and assignments. We recommend that officer MOS 35E skills be expanded to include those necessary to direct the activities of the current 97E and 351E MOS. We also recommend that only experienced 35E be designated to command CI/HUMINT organizations. To assure such assignment, we recommend the creation of a 35E certification program that designates training and experience criteria for each command position.
9. Conclusion.
a. Our Army is evolving toward a future operational environment in which CI/HUMINT plays a critical role. Force XXI concepts demanding precise, distributed, simultaneous operations translate as requirements for equally precise, multi-echelon, internetted CI/HUMINT operations.
b. Our concept for Army CI/HUMINT XXI gives the warfighter and senior decision maker the CI/HUMINT support his operations demand and soldiers deserve. We offer an internetted CI/HUMINT force capable of surging support at critical times and places, both in peace and on the battlefield; we bring precision collection and analysis critical for mission execution and force protection; and we bring smart, tactically proficient soldiers, fully capable of paralleling the commander and his evolving situational requirements.
c. Meeting our CONOPS, however, requires substantial improvements in each of the DTLOMS categories. We need holistic, national-to-tactical doctrine; realistic training simulations; leaders capable of leveraging CI/HUMINT with specific taskings; organizations postured for surge support; common materiel connectivity from national to tactical; and, new or consolidated soldier skill categories.
d. We base our recommendations on a top-to-bottom review of CI/HUMINT functions, as viewed through the prism of Force XXI and Intelligence XXI. Appendix 1 details CI/HUMINT support to Force XXI patterns of operation. Appendix 2 outlines how CI/HUMINT functions relate to Intelligence XXI tasks. In appendix 3, we provide detailed tables specifying CI/HUMINT requirements by echelon, while appendix 4 provides some of our thoughts concerning DTLOMS impacts. Finally, as our review was from top-to-bottom, we provide in appendix 5 some comments concerning Combined operations and, in appendix 6, some current CI/HUMINT areas we suspect rest outside the Army CI/HUMINT XXI charter, areas we view as outsourcing candidates. Appendix 7 addresses communications requirements and helps highlight some considerations planners must address when integrating long range surveillance into the CI/HUMINT system. Appendix 8 contains classified discussions regarding Army HUMINT collection missions in comparison with the Defense HUMINT Service.
Appendices:
1-CI/HUMINT and the Force XXI Operating Environment
2-CI/HUMINT Functions Relative to Intelligence XXI Tasks
3-CI/HUMINT Requirements, Capabilities and Functions by Echelon
4-CI/HUMINT CONOPS Impact by DTLOMS
5-Combined CI/HUMINT Operations
6-CI/HUMINT Outsourcing Candidates
7-Army HUMINT Collection (published separately)
Appendix 1: CI/HUMINT and the Force XXI Operating Environment
1. General. To be effective, Force XXI CI/HUMINT activities must be consistent with and readily adaptable to Force XXI operational patterns. CI/HUMINT will operate across each of the six patterns (TRADOC PAM 525-75, Intel XXI). Although support to "Protect the Force" will be a critical CI/HUMINT mission, CI/HUMINT will be a key collector and processor of information throughout each of the patterns, especially in a HUMINT rich SASO environment.
2. Protect the Force. CI/HUMINT will play a dominant role and be the intelligence main effort in supporting commander and senior decision maker protect the force responsibilities. CI/HUMINT will provide key information, intelligence and insights for success in the force protection mission.
a. Assets deployed to a theater of operations may be a joint and/or combined team drawn from national/strategic, operational, tactical or other service components. They will integrate CI and HUMINT functions and these teams may operate independently or in groups. LRS teams may work directly for the JTF commander if the JTF CDR is the Corps Cdr or combined. SOF elements will always work for the JTF commander. An architecture will link SOCCE/LRS base stations to allow fusion of multiple reports and access to databases across echelons, military services, and other agencies. Commanders will be able to draw from national HUMINT reporting by the DHS, US State Department, Central Intelligence Agency (CIA), and SOF. They will take advantage of Army strategic CI capabilities through connectivity or resource tailored support packages pushed down to the operational and tactical levels. For example, a team of strategic CI/HUMINT analysts providing connectivity to national databases; a team of technical experts providing a Technical Service Countermeasures (TSCM) capability; or a team of specialists conducting an Offensive CI Operations (OFCO).
b. Automated processing and analysis capabilities will provide graphical displays that show relationships and linkages between events, personalities, and factions. Whether in the sustaining base or while deployed, the commander facing a force protection problem will have CI/HUMINT tools that allow him to understand the threat, identify friendly vulnerabilities, and choose from a set of protective measures. Then, working with CI/HUMINT and other security and force protection specialists, the commander can direct a solution, implement preventive actions, and measure effectiveness of force protection programs.
c. CI/HUMINT will work closely with the other battlefield operating systems (BOS) to ensure the best possible support to force protection. For example CI/HUMINT will maintain a close working relationship with the military police corps and joint law enforcement assets. This will include information sharing, source deconfliction and integrated operations as situations dictate. This will require close coordination in planning and executing operations such as screening at traffic control points, handling enemy prisoners of war (EPW) and displaced civilians, performing cordon and search operations, conducting threat and vulnerability assessments, implementing population control measures, and tracking threat personalities, to name a few. This will require like communications and automation capabilities, source and information data bases, analytical methods, and common access to a set of files and information.
3. Project the Force. Projecting the force will require CI/HUMINT capabilities that are rapidly deployable. To leverage the full capability of CI/HUMINT, early deployment of CI/HUMINT assets will be essential. In some situations, CI and HUMINT resources may deploy well before combat forces. They will provide deploying combat forces direct and immediate contact with US Country Teams, DHS, and host nation intelligence and security services. In this way, CI/HUMINT develops and provides critical threat information to commanders.
a. Sustaining base CI assets will support the movement of forces and equipment through ports of embarkation, and provide national level CI analysis, as well as current data base holdings, geared to the target area and threat. Forward deployed CI assets will provide coverage of ports of debarkation and/or sanctuary facilities. The end-state vision will require split-based and push-pull broadcast intelligence capabilities, including the ability to receive updates enroute. Deployed assets will retrieve and update information on the area of operations and provide reporting back into the national system to support I&W, IPB, and trend/link analysis. CI/HUMINT reporting and analysis will support the planning and decision making process with accurate, relevant and timely information.
b. Deployed teams will require automated language translation systems for interrogations, document exploitation and source operations. They will also require linguists organic to the teams to accomplish their collection mission.
c. LRS/SOF units should organize themselves into rapidly deployable force projection packages consisting of individual teams and a command, control and communications cell. These elements have special considerations in this operational pattern because of their special ingress and egress needs.
4. Sustain the Force. CI/HUMINT support to sustaining the force will be continuous. From sustaining base or sanctuary to deployed areas through various phases of the operation and return, CI/HUMINT support will be key in sustaining a viable and ready force.
a. This will include CI/HUMINT support to the movement of supplies, equipment and personnel; the protection of key logistics facilities and critical lines of communication; operations in the friendly rear areas, area support groups, and communications zone (COMMZ); key operating bases and airfields; and protecting military applications of sensitive technology.
Collection of information will be key; however, the primary tool will be assessments and analysis that combine skills of not only CI/HUMINT, but also physical security, public affairs, automation, signals, and other specialists.
b. As the contingency matures and mission evolves, we will tactically tailor modular and scaleable CI/HUMINT assets and capabilities to meet mission requirements. This may require a mix and series of additional collection teams, operational management teams, and teams in Analysis and Control Elements (ACE) working with intelligence officers, operations staffs, collection managers, technical support teams, and military intelligence units.
5. Gain Information Dominance. CI/HUMINT plays a critical role in achieving information dominance. By providing insights into adversary intentions, senior decision makers and commanders can plan and execute friendly operations accordingly. Concurrently, CI/HUMINT contributes to the security of friendly information and operations.
a. Success will be through vigilance and keen awareness of the threatís ability to employ all the elements of C2 attack. Through source operations, CI/HUMINT must detect the threatís use of deception and psychological operations and penetrate adversary OPSEC measures. Conversely, CI/HUMINT must understand the threatís efforts to penetrate friendly OPSEC efforts and strive to disrupt or defeat those efforts. Through MDCI analysis, CI/HUMINT must predict what the threat views as HPTs and HVTs.
b. Using collection, operations, and investigative techniques, CI/HUMINT must determine the threatís access to technology that makes our electronic systems susceptible to exploitation. This will require capabilities at all echelons and substantial shared databases. Software that checks the status of WAN/LANs and detects intrusion attempts will be a key tool. The flow of intelligence from CI/HUMINT teams and analysis elements will provide concise pictures of the enemyís defensive or offensive posture, his operations to disrupt our rear areas and information nodes, and the morale and will of enemy troops and units.
c. CI/HUMINT will support C2W efforts. CI/HUMINT will have an important role in deception and psychological operations that support information dominance and shaping the battlespace. In support of friendly OPSEC initiatives, analysis will show how the enemy sees the friendly picture. CI/HUMINT source operations will be critical components of C2 attack operations.
d. CI/HUMINT will work closely with civil affairs (CA) and psychological operation (PSYOP) units in a mutually supporting role. CA and PSYOP will have wide access across the battlefield including potential sources. Sharing information between CI/HUMINT and these elements will enhance each othersí capabilities and focus assets for better utilization, eliminate duplication, and answer information gaps that may exist. As in working closely with the military police corps and joint law enforcement, joint CI, CA, and PSYOP operations will require common automation/ communication, reporting, data basing, and analysis capabilities.
6. Shape the Battlespace. CI/HUMINT will be crucial in shaping the battlespace. Reporting from interrogations and source debriefings will be essential as the commander gains an understanding of the adversary and the battlespace. More importantly, the fusion of CI and HUMINT reporting allows the commander insights into the enemyís intent.
a. CI/HUMINT sources may forecast future enemy operations. Long range surveillance units will augment, complement and trigger other collection systems that are more vulnerable to limitations such as weather, range, terrain masking, and enemy countermeasures. LRS units also allow commanders to gather timely information that does not need lengthy processing and analysis. Interrogators will give a unique vision of the adversary, face-to-face. The morale, unity, health and even numbers of EPW will provide concrete indicators of the enemyís will to fight. CI and HUMINT activities in friendly rear, assembly, and support areas will provide intelligence that describes the enemyís strategy to disrupt our operations and logistics.
b. Developing a picture of the adversaryís intelligence efforts will allow the commander to focus his security efforts and the activities of CI elements to defeat or disrupt the threatís collection efforts. These insights will help determine the enemyís overall strategy or intent and the possible direction of future offensive efforts.
c. CI/HUMINT elements at all levels will direct efforts to provide focused intelligence. This will require connectivity from collection teams and LRS units to operational management elements and ultimately into the Analysis and Control Team and/or the Analysis and Control Element (ACE) for inclusion in the all source picture.
d. CI/HUMINT servers, databases, and collection management systems that are a part of and readily parse into the All Source Analysis System (ASAS) will give the needed push/pull capability across echelons. This will ensure the timeliness of CI/HUMINT information, prevent false confirmation and allow necessary quality control to prevent adversary exploitation of CI/HUMINT.
e. CI capabilities in sanctuary will provide another set of tools to commanders as they set battlefield conditions and shape the battlespace. OFCO provides the commander a capability to directly interact with adversary intelligence elements.
f. Mass movements of EPW and/or displaced civilians, as well as the actions, morale, attitude, and political leanings of a friendly, hostile, or even neutral populace, will have a dynamic impact on the commanderís ability to shape the battlespace and eventually conduct decisive operations. CI/HUMINT, working closely with military police, CA, and PSYOP, will be the primary means of gathering information and analyzing this phenomena. In a SASO, it will be important for CI/HUMINT to merge with other elements such as medical, veterinary, engineer, or legal services to conduct operations supporting force protection and information collection for I&W, IPB, and situation development.
7. Decisive Operations. CI/HUMINTís role in decisive operations is to report information regarding the adversaryís center of gravity. CI will provide opportunities to neutralize adversary collection at critical junctures. In a SASO environment, CI/HUMINT will be the most viable intelligence source during the height of the operation. During a more intense, fast-paced Major Regional Conflict (MRC), CI/HUMINT will support BDA and offer insights to future adversary activities. LRS teams will be capable of sending real-time SIR to the commanderís PIR in reconnaissance or surveillance missions, conduct target acquisition missions on HPT or HVT immediately followed by BDA of those targets. However, at the conclusion of the MRCís decisive operation and transition to a more static environment, CI/HUMINT will again play a more dominant role.
a. Not only will CI/HUMINT support conventional units, but there will be a continuing need for tailored CI/HUMINT support to special operations forces and special mission units as they conduct specialized operations.
b. Interrogation of prisoners of war, defectors, and line crossers; and debriefing refugees/émigrés and displaced persons will offer timely information to commanders on the state of adversary forces.
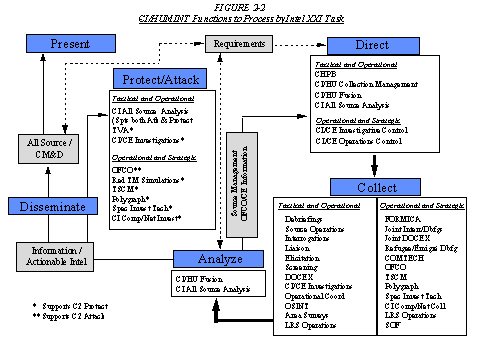
Appendix 2: CI/HUMINT Functions Relative to Intelligence XXI Tasks
1. TRADOC Pamphlet 525-5, Force XXI, outlines our future force concept. TRADOC Pamphlet 525-75, Intelligence XXI, details how Army intelligence will support execution of Force XXI operations. Table 2-1 below places Army CI/HUMINT XXI in the context of Intelligence XXI, essentially identifying those functions CI/HUMINT will pursue in Army XXI and their relationship to our future Intelligence XXI tasks.
Figure 2-1
CI/HUMINT and Intelligence XXI Tasks
|
Intelligence XXI Tasks |
CI/HUMINT Functions |
|
Direct |
CI/HU Prep of the Battlefield (CHIPB) CI/HU Collection Management CI/HU Fusion CI All Source Analysis ----------------------------------------- CI/CE Investigative Control CI/CE Operations Control |
|
Collect |
Debriefings Source Operations Interrogations Liaison Elicitation Screening Document Exploitation (DOCEX) CI/CE Investigations Operational Coordination Open Source Intelligence Area Surveys ----------------------------------------- FORMICA Joint Interrogations/Debriefings/DOCEX Refugee/Émigré Debriefing COMTECH Offensive CI Operations (OFCO) Technical Surveillance Countermeasures (TSCM) Polygraph Special Investigative Techniques CI Computer/Network Collection |
|
Analyze |
CI/HU Fusion CI All Source Analysis |
|
Disseminate |
CI/HU Fusion CI All Source Analysis |
|
Present |
CI/HU Fusion CI All Source Analysis |
|
Attack |
CI All Source Analysis ----------------------------------------- Offensive CI Operations (OFCO) |
|
Protect |
CI All Source Analysis Threat / Vulnerability Assessment (TVA) CI/CE Investigations ----------------------------------------- Red Team Simulations Technical Surveillance Countermeasures (TSCM) Polygraph Special Investigative Techniques CI Computer/Network Investigations |
* Note: Items below the dotted lines within the functions column denote that these are strictly operational level functions, or
functions that strategic CI/HUMINT can push down to the operational and/or tactical level.
Appendix 3: CI/HUMINT Requirements, Capabilities and Functions by Echelon
1. This section addresses CI/HUMINT requirements by echelon, identifying programs, functions, or tasks of clear value to the Army XXI warfighter. Our discussion begins with strategic CI/HUMINT, and follows with details concerning operational and tactical CI/HUMINT. Consistent with Army doctrine, we discuss each echelon within the context of the six intelligence functions (I&W, IPB, Situation Development, Targeting Support, Force Protection, and BDA), additionally highlighting echelon specific functions or programs as necessary.
2. Strategic CI/HUMINT. Strategic CI/HUMINT fulfills a variety of unique functions while simultaneously supporting operational CI/HUMINT with focused support and resources. Our view of strategic CI/HUMINT in Army XXI includes the following:
a. General. There will be a continued need for Army CI/HUMINT to satisfy the requirements identified in TITLE 10, 18, & 50; Executive Order 12333; DoD directives and Army Regulations.
(1) The Army has continuing responsibility to conduct the full range of overt HUMINT and HUMINT-related operations in peace, crisis, contingencies, and war. These operations are thus complementary to (not duplicative of) those of DHS. These operations include FORMICA collection, DOCEX, reconnaissance, interrogations, refugee/émigré debriefing, and liaison. The focus of these operations is on Army specific requirements satisfying the tactical and operational needs of Army commanders. Army overt HUMINT collection operations may be conducted unilaterally or jointly with DHS, as determined by the local operational environment. In all cases, however, the Army will coordinate these operations to ensure the effective application of resources against Army requirements without duplication of effort.
(2) Strategic CI will continue to have a wide charter, which includes satisfaction of combined and departmental requirements and employing specialized CI capabilities down to the operational and tactical levels as needed. A strategic CI capability is critical to Army XXI success. Strategic CI will provide key support to both sustaining base and deployed forces, and will be crucial to meeting force protection, information operations, and technology protection missions. To this end, our strategic CI force must be capable of surging support between operational & tactical requirements.
(3) CONUS-based strategic CI will have unique technical and mission capabilities and the ability to leverage the CI capabilities of the FBI and CIA to meet the needs of Army, tactical, and operational commanders. It is the Armyís principal interface with national CI and HUMINT organizations (FBI, DIA, CIA), and with national and local law enforcement for CI purposes, less those managed by tactical and operational forces when deployed in joint or combined operations. It provides specialized CI support to activities such as Defense Special Weapons Activity, Defense Mapping Agency, Forces Command, Training and Doctrine Command, Army Materiel Command, Signal Command, and all Army MACOMs across the CONUS sustaining base and overseas.
(4) OCONUS based strategic CI has the charter to provide dedicated US Army CI/HUMINT support to the SACEUR headquarters and its major subordinate NATO military headquarters. It is the only Army CI/HUMINT organization with a full-time combined mission. It will conduct the full range of strategic CI functions in the combined environment, as well as operational and tactical CI/HUMINT functions.
b. Strategic CI/HUMINT has the following primary roles and responsibilities.
Table 3-1
Strategic CI/HUMINT Roles and Responsibilities
|
1. Provides the CI/HUMINT connection between strategic/departmental levels to the national intelligence infrastructure. It supports Unified Commands and national agencies.
2. Plans and executes the full range of CI/HUMINT functions to satisfy Army Title X requirements.
3. Projects tailored CI teams with technical, collection, investigative, operations and analysis capabilities to reinforce and support operational level and deployed commanders.
4. Conducts advanced CI and HUMINT training for Department of the Army (DA) and DoD in special investigative, collection and operations techniques. This includes the Technical CI School and the Advanced Foreign CI Training Course. Also provides resources to the Military Operational Training Course. (see paragraph 2c below)
5. Manages Army-level CI/HUMINT collection operations to meet DoD and Army intelligence information needs and to populate databases to meet lower echelon IPB requirements.
6. Serves as the Army executive agent for dedicated CI Support to International Treaty verification, DoD Acquisition Systems Protection Programs, and all Army and several national Special Access Programs.
7. Provides dedicated CI support to Special Operations Forces (SOF) and Special Mission Units (SMU) by working against FISS efforts to collect intelligence on SOF and SMU. CI mission responsibility will be divided between organic CI assets assigned to SOF units, and the CONUS- based strategic CI assets for dedicated support to various SOF and SMU missions.
8. Supports DoD Intelligence Systems Security Site Based Accreditation and SCI Contractors.
9. Acts as the Armyís executive agent for Freedom of Information Act/Privacy Act requirements for all HUMINT and CI record information. |
c. With respect to item 4, Table 3-1 above, identification of this responsibility stems from a July 1985 Memorandum of Understanding (MOU) between the Commander, USAICS and Commander, INSCOM. This MOU and its delineation of roles and responsibilities deserves careful review to ensure continued USAIC and INSCOM training synergism in support of Army XXI. Of particular interest is ensuring complementary programs of instruction; equitable burden sharing; and applicability to soldiers ECB.
d. Strategic CI/HUMINT will support all six intelligence functions as it answers the specific commander critical information requirements delineated in Table 3-2.
Table 3-2
Strategic CI/HUMINT Requirements
|
Intelligence XXI Functions |
Commander Critical Information Requirements |
|
Indications and Warning |
CI specific: Detect and assess changes in the political, social, military, and economic situation in the threatís homeland which impact its intelligence capabilities and will to use them. Assess changes in FISS capabilities and intentions towards Army forces, information, key technologies, C4I systems and nodes. Assess foreign capabilities to acquire key technologies in their military force modernization programs and systems. Assess foreign governmental and societal stability with a view towards identifying and predicting emerging terrorist threats.
HUMINT specific: Develop enemy ground force capabilities to include military doctrine, force structure, operations, tactics, combat, CS and CSS systems. Develop current and future foreign ground force TO&Es for all organizations from Army to battalion level. Develop databases outlining the Information Warfare capabilities of specified countries. Define select characteristics and performance data on foreign armor, anti-armor, air defense, IEW, missile, engineer and mine warfare, aircraft, and soldier systems. Acquire and exploit foreign systems with military applications to determine potential threats to US forces and systems. Acquire and create a database of signatures on all foreign C4I and weapons systems. |
|
Intelligence Preparation of the Battlefield |
CI specific: Populate and maintain the Modernized Integrated Database and other DCIIS based systems to provide baseline information on foreign orders-of-battle, foreign intelligence and security services organizations, collection capabilities, intentions and methods of operations, and infrastructure; determine threat courses of action to acquire information detailing friendly C2/C4I capabilities and networks, critical technologies and associated efforts and facilities, key infrastructure, and order of battle. ID and locate belligerent personalities under suspicion of or wanted for crimes under the provisions of international law.
HUMINT specific: ID, collect, and process biographic data on key foreign figures, both civilians and military, having an impact on tactical, operational and strategic decisions. |
|
Force Protection |
CI specific: ID and assess the capabilities, intentions, and operations of foreign intelligence and security services to acquire essential information on forces, operations, C2 and C4I capabilities, and on research and development program information and technologies embedded in current and future Army systems. ID and assess the capabilities of foreign governments to protect sensitive information and technologies contained in Army systems or programs under consideration to be shared/sold to those countries. ID and assess capabilities and intentions of terrorist groups who pose a potential threat to US Army personnel, facilities, or operations. Detect, locate, identify, process, track, report, counteract, and exploit all-source intelligence collection threats against friendly forces, research and development and acquisition activities, critical technologies, C4I systems and networks, and personnel. ID critical friendly facilities, forces, information nodes and vulnerabilities. ID threat paramilitary forces. Determine countermeasures required to deny a given threat information on friendly intentions, plans and operations. |
|
Situation Development |
CI specific: Detect, locate and ID foreign intelligence and security service (FISS) collection members, groups, capabilities, intentions. Detect, locate and ID FISS and deliberate security /hacker efforts against friendly C2/C4I systems and processes. Detect, locate and ID terrorist groups, support cell/structure, and terrorist sponsor organizations/nations, methods and intentions. Detect, locate and ID US Army personnel engaged in SAEDA, their methods and intentions. Detect, locate and identify threat SOF/SMU elements. Update biographic data on key foreign intelligence, military, security and law enforcement figures, both military and civilian. Detect and report foreign intelligence activities directed against friendly forces, operations, installations, materiel and Army personnel.
HUMINT specific: Detect, locate, identify, and report WMD, advanced technology weapons, TBM, to include C4I, delivery systems, and storage. Detect, identify, locate, and report the location, strength, and capabilities of threat ground forces. Identify and report activities related to the acquisition of new military capabilities. Determine and track status of US and allied POW/MIA. |
|
Target Development and Support to Targeting |
CI specific: Detect, identify, track and nominate high payoff targets, i.e., military critical technologies, special mission units, research, development and acquisition centers, sensitive facilities, special access programs, critical C4I nodes and networks, etc., for CI/CE investigations, collection emphases, RED TEAM and CI special operations, CI projects and other CI security countermeasures. |
|
Battlefield Damage Assessment |
CI specific: ID and report from the CI perspective damage to information, technologies, forces, C4I systems, materiel, and personnel caused by FISS, terrorism, and deliberate security compromise activities, for situational development, friendly reconstitution and sustainment, and for CI target development and retargeting requirements.
HUMINT specific: ID and report damage inflicted on the threat to evaluate threat operational status. |
d. Additional Strategic CI Only Requirements. Strategic CI will perform the following functions to accomplish its Army-wide mission.
Table 3-3
Strategic CI Functions
|
Strategic CI Function |
Discussion |
|
CI All-Source Analysis
Red Team Simulations
CI/CE Investigations
CI Computer Systems/Network Collection and Investigations
Offensive Counterintelligence Operations (OFCO)
CI Special Operations
Technical Surveillance Countermeasures (TSCM)
Polygraph
|
This will be a major undertaking at this level in order to support CI analytical efforts Army-wide, and provide a split-based push and pull capability for CI information and databases to deployed forces. They will accomplish this task with a strategic all-source fusion center for dedicated CI and counterterrorism analysis and production for the Army.
Red Team Simulations attempt to replicate foreign intelligence methods for penetrations and collections of a specified target. This is a key CI/HUMINT activity for evaluating units and determining vulnerabilities to threats so commanders may take appropriate protective measures. This function will require a coordinated effort between signals, communications, automation, physical security, and criminal investigation specialists.
Controls all Army CI/CE investigations, and conducts the most sensitive CE investigations. This includes the use of sophisticated special investigative techniques.
This will involve the detection, investigation and/or exploitation of electronic collection directed against military and commercial computer systems and networks involving Foreign Intelligence and Security Services (FISS) and other foreign collection efforts, and deliberate sabotage, hacking or other unauthorized efforts to collect, manipulate, degrade or destroy Army information resident on those systems and networks.
This will continue to be a strategic CI function due to the nature and scope of these operations. However, OFCO may be the only means to answer particular operational or tactical level CI/HUMINT requirements; therefore, OFCO assets and information will be readily available to push down to succeeding level as the situation dictates.
This includes operational/ technical support to investigations; complex defensive source operations, and special techniques used to support Information Warfare.
TSCM is a key capability in C2 Protect. We must train, equip, and properly use a viable and deployable TSCM force in the active Army. Although located at the strategic level for control and management, strategic CI must ensure the capability to support operational and tactical operations.
This will include CI scope polygraph examinations as well as support to CI operations. We will conduct examinations on local hires having local access authorization (LAA) or who provide information which US forces may act upon, and test translators/ interpreters. CI operations/ investigations will employ the polygraph when questions arise which are not otherwise verifiable. We will use it anytime a source provides time-sensitive information which may have a direct impact on the safety of US forces and the information is not otherwise verifiable. Although the Army will control this function at the strategic level, we will be able to push this capability down to the lowest level through the force projection brigade into multiple theaters of operation. |
3. Operational CI/HUMINT Roles and Requirements
.
a. General. CI/HUMINT at the operational level is the nexus between tactical and strategic CI and HUMINT operations. In this role, CI/HUMINT in the Force Projection Brigade will have four primary responsibilities.
(1) First, they will have an early entry and pre-hostilities requirement to establish CI/HUMINT in the area of operations for ground intelligence, threat, and force protection reporting. They will establish links to host nation and regional agencies for liaison and information gathering in contingency areas; and conduct collection efforts external to, but focused on, the target area. By maintaining a continuous forward deployed presence and collection emphasis, their operations will be critical in answering many pre-deployment and pre-hostility requirements across all echelons.
(2) The second role for operational level CI/HUMINT will be a direct result of support they provide by their forward deployed presence and activities. A pre-deployment presence will give them a force reception capability. As such, they become key elements for protecting the force through the entire force projection pattern. They will be the only CI/HUMINT capability on the ground as tactical forces conduct entry operations and establish their own areas of operation. By their established presence, operational CI/HUMINT assets will be able to pass on key intelligence and threat information to arriving forces, and eventually do a hand-off to tactical level CI/HUMINT when and where appropriate.
(3) Operational CI/HUMINTís third role will be reinforcing the tactical CI/HUMINT effort. In most cases, this will involve pushing operational CI/HUMINT assets and capability down to the tactical level, e.g., LRS teams, SOF Teams, CI investigative and HUMINT debriefing capability. In fact, during an SASO, it is likely that tactical commands will require operational level assets from the onset. This is especially true when we consider the likelihood that the Army Component will be an ECB organization under a major Army or joint command. In essence, the ECB commander will become the operational level commander and will require the CI/HUMINT functionality associated with operational levels of command. Conversely, we may pull operational assets to support strategic level efforts.
(4) The fourth role for operational CI/HUMINT will be as a conduit and host to bring Army strategic CI and national HUMINT assets and capabilities into the deployed area of operations. In this way, operational and tactical commanders will be able to leverage the full range of national/ strategic HUMINT and CI capabilities when and where needed. Army strategic CI will push capabilities and packages into the area operations through the Force Projection Brigade.
Table 3-4
Operational CI/HUMINT Requirements
|
Intelligence XXI Functions |
Commander Critical Information Requirements |
|
Indications and Warning |
ID the threat countryís intentions and ability to sustain the fight. ID adjacent countriesí impact on the JTF mission. Detect changes in threat countryís intelligence and security serviceís posture and intentions. |
|
Intelligence Preparation of the Battlefield |
Develop ground, paramilitary and other selected orders of battle on regional threat forces. Describe the offensive and defensive medical/bio-scientific capabilities of the belligerent countries. Describe transportation and movement networks, egress and ingress routes in JTF battlespace. Describe threat doctrine, concepts, and targeting philosophies and their impact on friendly operations. ID significant political, social and cultural factors in belligerent countries that impact on friendly operations. Describe doctrine, concepts, and targeting philosophies of belligerent countries and their impact on friendly operations. ID and locate belligerent personalities under suspicion of or wanted for crimes under the provisions of international law. |
|
Force Protection |
Detect, identify, locate, track, and report threat elements to friendly forces within JTF battlespace and probable threat intentions. Identify and report on threat paramilitary forces. ID critical friendly facilities, forces, information nodes, and vulnerabilities. Define the intelligence threat to the friendly force mission external to the JTF battlespace. Determine countermeasures required to deny the threat information on friendly intentions, plans, and operations. Evaluate the success of friendly C2W operations. Detect, identify and report internal security threats to friendly forces in the host country. Detect, prevent, or counteract threat C2W/RISTA efforts directed against friendly forces within the JTF battlespace. Detect, locate, identify, and counter terrorism. Identify and assess host nation forceís ability and willingness to protect friendly resources and personnel. |
|
Situation Development |
Analyze the political, social and economic situation in the threatís homeland to determine threat capabilities and will to fight. Detect, locate, identify, and track threat SOF elements. Update biographic data on key foreign figures, both civilian and military. ID and report opportunities for friendly C2W operations. Detect and report foreign intelligence activities directed against friendly operations, forces, installations, and materiel. Detect, locate, identify and track key threat battlefield C4/RISTA nodes within the JTF battlespace. Report and track status of friendly prisoners of war and personnel missing in action. Detect, locate, identify and report new obstacles in JTF battlespace. Identify effects of weather, refugees, and combat/combat service support operations on friendly and enemy lines of communications. |
|
Target Development and Support to Targeting |
Detect, identify, locate, track, and nominate high payoff targets for lethal/non-lethal attack (fires, PSYOP, EW). Differentiate between decoys and actual high priority targets. Detect, locate, identify, track, and report threat SOF within the JTF battlespace. ID potential non-lethal targets (economic centers of gravity, cultural population centers, etc.) for potential exploitation by friendly PSYOP, IW, CA, and CI forces. |
|
Battlefield Damage Assessment |
ID and report damage inflicted on the threat to include estimated casualties to evaluate threat operational status for situation and target development and retargeting requirements. ID and report damage to threat reconstitution and sustainment efforts including major ports, airfields, and logistics facilities. Determine and report damage to transportation networks, main lines of communication, telecommunications, information networks and processes, and logistics facilities within the JTF battlespace. |
b. Operational level CI/HUMINT forces will support all six intelligence functions as they respond to operational level requirements as shown in Table 3-4. CI/HUMINT activities executed at this level will be essential to the success of Army XXI operations. The Force Projection Brigade, the operational level military intelligence unit, will provide a forward presence during pre-hostilities and, as such, will play a crucial role during preparing, projecting, protecting, and sustaining the force. The challenge then will be to shift from peacetime activities in a Unified Commanderís AOR to focus on a specific crisis while maintaining an AOR wide overwatch capability.
4. Tactical CI/HUMINT Roles Requirements.
a. To meet CI/HUMINT requirements at ECB, we will either put requisite capabilities resident at ECB or have the ability to push capabilities down to the lowest tactical level from the operational level (force projection brigade). It is important to note that in the FORCE XXI operational environment, a tactical brigade, division, or corps could be the primary ground component and will require the CI/HUMINT functionality associated with operational levels of command.
b. Corps, division, and tactical brigade missions and requirements will be similar and overlapping. CI/HUMINT capabilities at echelons corps and below (ECB) will be necessary in a MRC and become even more critical during a SASO. CI/HUMINT will support all six intelligence functions in response to tactical level requirements as shown in Table 3-5. The challenge then becomes the ability to shift from a training and readiness environment that does not routinely challenge all CI/HUMINT soldiersí skills to high OPTEMPO operations directed at a specific adversary.
Table 3-5
Tactical CI/HUMINT Requirements
|
Intelligence XXI Functions |
Commander Critical Information Requirements |
|
Indications and Warning |
Provide information on the enemyís intention to disrupt friendly operations while in sanctuary, enroute or in assembly areas. |
|
Intelligence Preparation of the Battlefield |
ID composition, disposition, strength, tactics, capabilities, C4I and training status of threat. ID threat perception of the friendly mission. ID the host nation infrastructure, intelligence/security organizations/ capabilities, local government, agencies, paramilitary organizations, and their intentions and capabilities. ID population demographics, location of noncombatant populations, social, cultural and economic issues, and areas of expected refugee flow. ID the perception of friendly operations by all governments, belligerent organizations, host country populaces and refugees. ID and assess all potential actions of belligerents that violate agreements, protocols, or laws. |
|
Force Protection |
Provide information on threat RISTA, subversive, sabotage and terrorist efforts while friendly units are in sanctuary, enroute, or in assembly areas to protect friendly information, personnel, equipment and operations. ID critical sites and conduct vulnerability assessments to include nomination of friendly High Value Targets (HVT). Maintain data on the identity and location of friendly and/or neutral personnel who may interfere with or disrupt operations. Conduct host country liaison. |
|
Situation Development |
ID violations of agreements by belligerent forces. ID and monitor changes to the political, economic and social environment that could have a major impact on friendly operations. Detect, ID, and locate threat SOF activities and agents, paramilitary sites and forces, and terrorist groups and their support structures. Maintain current location of US nationals and NGOs, and ID friendly agency operations. |
|
Target Development and Support to Targeting |
ID and locate enemy conventional and unconventional organizations and their leaders; critical LOCs, airfields, ports and logistics bases to target accuracy requirements for lethal or non-lethal attack. |
|
Battlefield Damage Assessment |
Collect and report damage to targets engaged by lethal and non-lethal means to include effects upon conventional and unconventional organizations, intelligence and decisionmaking processes, RISTA capabilities, weapons systems, and threat personnel. |
5. Common Operational and Tactical CI/HUMINT Programs or Functions
.
a. The following is a detailed discussion of CI/HUMINT functions at the tactical and operational levels. These functions form the common operating concepts that will drive the development of automated tools and functionality for complete integration into ASAS and DoD CI Integrated Information System (DCIIS). Functions identified in subparagraphs (1) thru (16) below are common to the tactical and operational levels. They are similar by design to achieve standardization and commonality for a truly seamless architecture. The primary difference is operational level products will reflect the different focus and needs of the operational level commander, and this is the first level where we satisfy Departmental (TITLE X) and Joint requirements. Functions identified in subparagraphs (17) thru (21) below are found only at the operational level. If tactical commanders need additional CI/HUMINT capabilities, they will pull them down from the operational level when and where needed.
(1) CI/HUMINT Preparation of the Battlefield (CHIPB): CHIPB forms the synthesis of CI/HUMINT thought and environmental applications, and teaches personnel "how to think" from a CI/HUMINT point of view. It applies in peacetime, transition to conflict, conflict, and transition back to peace. It applies to all echelons and all types of CI and HUMINT operations. Following are some of its more specific products.
(a) CHIPB will establish an in-depth understanding of friendly missions and operations; and will support detailed CI/HUMINT planning, staff coordination, mission analysis, and synchronization.
(b) CHIPB will define the operating environment and the effect of that environment on both friendly and enemy forces from a CI/HUMINT perspective. This will include detailed demographics, population, politics, culture, language, history, ethnicity, religion, military, and terrorism; information on police and other security forces, governmental agencies and databases, and economic systems; and a detailed look at information structures, lines of communication, and centers of gravity, to include attitudes and intentions.
(c) CHIPB will look at specified pieces of terrain, critical nodes, and associated friendly centers of gravity for a given operation or function at every echelon. Through this process, CI/HUMINT assets will assist a commander in developing Essential Elements of Friendly Information (EEFI) that require protection and association to a friendly center of gravity. At the strategic level, this could be a sensitive technology or operation by an Army special mission unit. At the operational or tactical level this could be any key facility, system or operation that is essential for successful Army XXI operations.
(d) CHIPB will identify threat methods of operation, organizations, and capabilities. The threat could consist of an intelligence organization (traditional), but could also stem from military, special purpose forces or terrorist surveillance for an operation, actual physical destruction, or psychological manipulation of friendly forces or indigenous personnel.
(e) CHIPB is the precursor to every CI/HUMINT mission at every echelon. It is essential for successful CI/HUMINT operations and drives counter-RISTA operations, OPSEC countermeasures and C2W planning.
(2) CI/HUMINT Collection Management - CI/HUMINT will participate in the collection management process to translate requirements into CI/HUMINT specific intelligence requirements (SIR) and specific orders or requests (SOR). Collection planning and synchronization at all echelons will be done primarily by defining CI/HUMINT specific SIR relative to the commanderís PIR. This process will not be separate from other planning. We will integrate and synchronize CI/HUMINT SOR with the overall intelligence effort. The system will allow tactical and operational units to leverage strategic CI and HUMINT capabilities. Mission management capabilities will be pushed to the lowest level necessary to coordinate operations.
(3) CI/HUMINT Single-Source Analysis - This function serves as a "single-source" fusion point for all CI/HUMINT reporting and operational analysis. CI/HUMINT Single-Source analysis correlates, collates, and quality controls all reports toward answering specific information requirements; builds and maintains source data bases and registries; creates and maintains links diagrams, association matrices, personality and installation databases, organization profiles, and other tools for use by all-source analysts and the CI/HUMINT asset manager; identifies collection gaps and opportunities for cross-cueing CI/HUMINT assets; disseminates CI/HUMINT reporting into the all-source data base; and presents a CI/HUMINT single-source picture of the battlefield for use by all-source analysts, as well as other disciplines and collectors.
(4) CI All-Source Analysis (CASA) - This function assesses threat capabilities to collect intelligence or interdict friendly forces through sabotage or terrorism; determines friendly vulnerabilities to that threat; and recommends countermeasures to protect friendly forces, facilities, and activities. CASA plays a key role in gaining information dominance and primarily supports the protect Intelligence XXI task. However, revealing information on the enemy collection and decision making process could uncover lucrative targets for attack and exploitation. CASA not only incorporates CI/HUMINT collection and fusion products, but leverages SIGINT, IMINT and other RISTA capabilities and resources to establish clear and concise counter-RISTA efforts at the tactical level. This function builds and maintains a detailed CI picture of the battlefield and/or environment by:
(a) Developing a detailed analysis of the threatís intelligence ability to exploit friendly vulnerabilities.
(b) Identifying and submitting requirements to fill CASA collection gaps.
(c) Receiving and reviewing collection manager taskings.
(d) Identifying opportunities for cross-cueing between intelligence disciplines to satisfy CASA requirements.
(e) Assisting CI/HUMINT Single-Source analysts and CI/HUMINT asset managers in focusing collection.
(f) Presenting CASA products which include CI estimates, target nominations, and other reports and graphics in support of C2W attack and protect.
(5) Threat/Vulnerability Assessment (TVA) - A TVA is a comprehensive evaluation of the security status of a unit or activity. The CI/HUMINT portion of the TVA will determine susceptibility to foreign intelligence collection and sabotage, subversion, or terrorism. It will also require the expertise of all-source collectors, intelligence information, and detailed CI analysis on the threat. When CI/HUMINT teams conduct a TVA they must know how to leverage the expertise of physical security specialists, public affairs, engineers, medical personnel, automation and signals specialists, unit operation sections, G3/S3, and others. TVAs are critical in ensuring continual evaluation of threat capabilities and friendly vulnerabilities.
(6) Debriefings - This will include questioning of US military travelers, soldiers, or employees in contact with a potential threat country or entity, or having access to a target area or information, as well as debriefing returned US POWs, hostages, and/or defectors. These are valuable sources that CI/HUMINT can leverage to meet tactical information requirements. These debriefings will also fill voids in DHS or other national-level coverage. These debriefing activities are an Army function to answer tactical, operational and senior ground component CCIR where DHS falls short in satisfying Army specific requirements (reference Secret DA DCSINT MSG, 181701Z SEP 96, subject: Army Tactical HUMINT Collection (U)).
(7) Source Operations - Source operations focus on collecting force protection and battlefield intelligence information which includes information on local terrorists, saboteurs, subversive activities, and other hostile activities affecting the security of deployed US Forces.
(8) Interrogations - This entails systematic questioning of a captured or detained source to obtain information of tactical intelligence, force protection or CI value.
(9) Liaison - This includes contact with host nation agencies and allied forces to collect information and/or coordinate operations.
(10) Elicitation - This will include contact and systematic questioning of civilians on the battlefield and non-detained sources to obtain information of tactical intelligence, force protection, or CI value. This will include regular elicitation/questioning of individuals in contact with US forces to determine knowledge relative to friendly CCIR.
(11) Screening - This includes the questioning of EPW/detainees to determine cooperativeness and knowledgeability, factors important in determining interrogation and evacuation criteria; questioning or review of persons on the battlefield at key times and places to obtain information of intelligence, force protection, or CI value; and regular questioning or review of individuals in contact with US forces to determine intelligence or CI interest.
(12) Document Exploitation - The translation of relevant foreign documents--document exploitation--will be a lucrative source of information and a viable function for gaining information dominance and shaping the battlespace.
(13) CI/Counterespionage (CE) Investigations - At the tactical level, incidents will occur that may have espionage, deliberate security violation, subversive, sabotage, or terrorist implications. Usually, these initial investigations are low level and require little additional investigative effort. However, an incident may turn into a prolonged investigation that would require additional work beyond the initial inquiry or more sophisticated methods and resources. CI investigative activity at this level includes the investigation of defectors and special category absentees.
(14) Operational Coordination - This includes any interaction with US agencies or other military service counterparts to coordinate operations, share information, or obtain assistance.
(15) Open Source Intelligence (OSINT) - The proliferation of INTERNET/World Wide WEB technology, and the ability to use automation to reach out and gather a wide range of information makes OSINT a viable CI/HUMINT function shared with other disciplines. OSINT will include extracting information from open sources such as target area publications and non-military broadcasts. This function will be critical for IPB, situation development and CHIPB. It will play a key role in our CI/HUMINT strategy as we determine friendly information vulnerabilities resulting from our own use of information systems. CI/HUMINT TVAs use OSINT to assess the availability of sensitive US Army and unit information to the general public and foreign entities.
(16) Long Range Surveillance Unit Operations (LRSOPS) Ė This includes the execution of any of the four primary LRS missions (surveillance, reconnaissance, target acquisition, and battle damage assessment) at either the tactical or operational level.
(17) FORMICA - This involves gathering information from US Army military and civilian personnel.
(18) Joint Interrogation/Debriefing/Document Exploitation - This function requires exploitation of human and document sources to satisfy joint requirements.
(19) Refugee/Émigré Debriefing - This action includes the systematic collection of operationally oriented information from displaced persons.
(20) COMTECH - This requires the collection of relevant technical information.
(21) Area Survey - This action consists of the systematic collection of infrastructure and associated information on target areas by CI/HUMINT personnel.
(22) CI/CE Investigations - Operational CI elements perform control and oversight of CI/CE investigations in the deployed area and employ specialized skills and techniques from initial incidents through completion/prosecution, as required.
(23) Special Operation Forces Ė SOF units due to their mission focus, operational patterns and capabilities require CI support in every phase of their operations. Most SOF units have organic CI/HUMINT and some have specially trained operational personnel who are potentially in virtually every CI function described above. Debriefings of SOF personnel returning from OCONUS missions is stored digitally using the Special Operations Debriefings and Retrieval System (SODARS). The SODARS program was developed to automate and store SOFís debriefing reports for retrieval by the US Special Operations community. Conventional CI/HUMINT elements should have an automated system to access this SODARS data on a day to day basis.
b. Operational level elements are smart receptacles for strategic CI plugs; e.g., Offensive CI Operations (OFCO), Technical Security Countermeasures (TSCM), Polygraph, Special Investigative Techniques, Red Team Simulations, and CI computer systems/network collection and investigations. They will control much of the operational activity of these assets in the deployed area of operations.
c. At the operational and tactical level , the LRS/SOF communications architecture must be modified in order to provide an automated system to process and disseminate into the ISR process.
(1) Requirements Management Ė When considering LRS and SOF operations and their integration into the overall CI/HUMINT picture, the capabilities of each element must be understood by the collection manager and synchronized on the collection plan. In order to realize the most efficient use of these assets the capabilities must be understood from the JTF to the lowest echelon. This synchronization is necessary in order to maximize the use of those LRS/SOF capabilities and ensure proper employment. This is best accomplished by the development of a Mission Rehearsal Tool (MRT) capability.
(2) Collection Ė The LRS/SOF force must ensure that it continues to develop the technology it needs to ensure integration into the overall intelligence picture. The key to this development piece is ensuring that the requirements for these common capabilities are stated in a Joint Operational Requirements Document (JORD). In addition, we have identified certain advanced technologies that could be applied to CI/HUMINT and we believe that there is an opportunity to also use these technologies for LRS/SOF operations. One area where advanced technologies are needed in communications. LRS needs the secure long range capability and it also needs short-range secure communications to send data, imagery or voice reports. An example of the long-range capability would be the SOFs AN/PRC-138 and the USAFís AN/PRC-139 for the short-range capability. It is also important that HUMINT have modern collection sensors such as Link ground sensors, handheld FLIR/electro-optics and digital camera capabilities.
We will see an increase in our adversaries capabilities to adversely affect the means and effectiveness of our collection activities. These capabilities include advanced encryption techniques, the use of lower power (decreased signature) communications means, use of alternative communication means(land lines, cellular, agile HF, multi-band, frequency hopping) and the effective use of OPSEC techniques. As a result, collection by airborne/overhead means may increasingly rely on cross discipline support and the inter-operation of HUMINT collection such as LRS/SOF/ABN. In this situation, we envision HUMINT elements as the insertion mechanism for technologies that will enable continued collection against our adversaries changing capabilities.
(3) Processing Ė within the area of processing intelligence information, the integration of intelligence derived from all intelligence disciplines is essential in providing a complete relevant picture for the commander. To accomplish this integration we see the need for an automatic reporting/dissemination system including integration of the Special Operations Forces Intelligence Vehicle (SOFIV), the addition of a HUMINT derived overlay onto the common relevant picture of the Joint Forces Land Component Commander (JFLCC) and the establishment of a HUMINT Product Library with similar capabilities to the Image Product Library(IPL). Another would be the development of deployable HUMINT databases. Currently, to conduct LRS, IPW and CI operations, the Operations sections must compose extensive RII/RFIs and send them to the ACE where ASAS cannot process the large number of RII/RFIs efficiently. To reduce the communications requirements and allow the independent deployment of HUMINT or LRS teams, deployable HUMINT/LRS data should be kept on mass storage devices in garrison and exploited in the field on common HUMINT/LRS workstations.
(4) Dissemination Ė The dissemination of the LRS/SOF derived information is another area of importance. Per 3-1, the dissemination spans echelons and branches of service in support of JTF JFLCC operations. Currently, LRS reports sent to the ACE are received on one system and then manually reentered onto ASAS. This slows down the entire HUMINT cycle, reducing the timely fusion of tactical HUMINT.
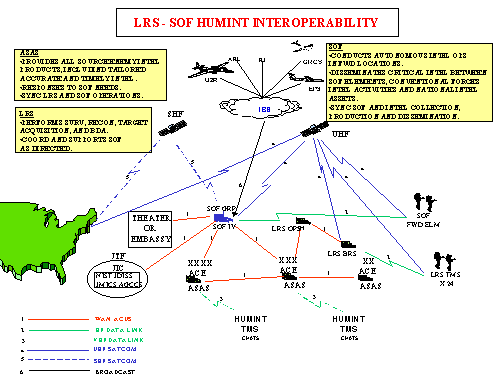 Figure 3-1
Figure 3-1
LRS/SOF Interoperability
Appendix 4: CI/HUMINT CONOPS Impact by DTLOMS
1. Our Army CI/HUMINT XXI CONOPS is certain to ripple across DTLOMS categories, dictating revisions and adjustments which accelerate our move toward Army XXI. It will drive the rewrite of various field manuals; impact institutional, organizational, and individual training initiatives; change our leader development programs; influence organization structures in TO&E and TDA organizations; and, create new requirements for materiel. Throughout all this, the individual soldierís needs must be addressed. This section details some of our ideas with respect to each DTLOMS category, and is a result of an ICT work group convened to specifically identify DTLOMS implications and a Council of Colonels review.
(1) Much of published MI Doctrine must be rewritten to better reflect how CI/HUMINT will support force projection and split-based operations in Joint and Combined environments consistent with the CONOPS.
(a) Significant revisions will need to be made to FM 34-1 (Intelligence and IEW Operations); FM 34-2 (Collection Management and IEW Synchronization); and FM 34-3 (Intelligence Analysis).
(b) More extensive revision will be required for FM 34-5(S)(HUMINT Operations); FM 34-52 (Interrogation); FM 34-60 (Counterintelligence); and FM 34-130 (Intelligence Preparation of the Battlefield). Revisions to FM 34-1 will ensure CI/HUMINT remains integrated with the larger military intelligence community consistent with its new capabilities. FM 34-130 revisions will focus on documenting those elements of CHIPB particularly relevant at the tactical level.
(2) There is, and will continue to be, a need to rapidly incorporate tactics, techniques, and procedures from lessons learned in operations into doctrinal literature. To systematize this, the Intelligence Center should:
(a) Modernize the research and writing process through use of automation and the INTELLINK.
(b) Establish a CI/HUMINT lessons learned hot line on INTELLINK.
(c) Make timely dissemination of CI/HUMINT lessons learned to CI/HUMINT organizations via INTELLINK.
(d) Hold periodic (quarterly, semiannual) in-progress reviews for CI/HUMINT.
(e) Establish stronger USAIC&FH interface with CALL and USAIS at Ft. Benning, GA to work CI/HUMINT lessons learned. Outsource compilation and databasing of TTP and lessons learned, if possible.
(3) We must continue to ensure CI/HUMINT contributions are understood, integrated, and documented through future Information Operations ICT efforts coordinated by the Intelligence Center and/or Combined Arms Center.
b. Organization. CI/HUMINT must have the capability to support peacetime and pre-deployment requirements and to tactically tailor support to each deployed echelon. Each echelon must focus on creating a CI/HUMINT force agile enough to shift from peacetime activities to conflict resolution. Our current force structure has significant CI/HUMINT capabilities at each level. Our CONOPS envisions a flexible surge capability best satisfied by ensuring standardized structures throughout the echelons.
(1) To facilitate team standardization, we recommend removing all CI/HUMINT assets(with the exception of Long Range Surveillance Units) from the MI Battalion DS Company (minus two personnel who will serve within the ACT) and consolidating these assets within the GS Company. This reinvestment enhances the Division Commanderís ability to place CXI/HUMINT where he needs them most--at the Brigades, with Aviation assets, or at the DISCOM. Consolidating current DS Company CI/HUMINT teams promises training efficiencies and an improved grade structure giving the Divisions the experience and expertise needed for tactical operations. (see Figure 4-1).
Figure 4-1. Standard CI/HUMINT Team Structure
(2) We recommend standard CI/HUMINT team structures at each echelon to ensure immediate support computability. A CI/HUMINT team in the Force Projection Brigade should be identical in personnel and equipment as one in a Division GS Company. This modular concept promises commanders "interchangeable, expandable, and tailorable force elements" (TRADOC PAM 525-5). It allows for maximum flexibility "to meet changing mission needs" and "maximize force requirements" (TRADOC PAM 525-68).
(3) Building standardized, modular CI/HUMINT team promises a task organization capability and integration potential that does not presently exist, but will be essential in meeting the dispersed geographical requirements of Army XXI. Consolidated, modular teams enhance operational flexibility. This "tailored" CI/HUMINT force can function in direct support of a tactical brigade, in general support of a division or corps, or anywhere in the theater of operations.
(4) The structures and positions at operational and tactical echelons will be similar. Standard structures ensure interoperability and facilitate tactical tailoring of CI/HUMINT for any contingency.
(a) CI/HUMINT Staff Officer (CHSO). The CI/HUMINT XXI concept will require a CI/HUMINT staff officer at major commands, corps, and divisions subordinate to the DCSINT and G2s. This is consistent with joint doctrine which suggests the need for a CI Staff Officer (CISO) and a HUMINT Coordination Element (HCE) at each unified command. The CHSO will facilitate transition of an Army Component, Corps, or Division staff to a JTF structure when required. The CHSO will require a minimal staff of two or three CI and HUMINT soldiers to perform the following:
(b) CI/HUMINT Team in the ACE (CHACE). The CI/HUMINT XXI concept requires a CI/HUMINT Team in the ACE of each Force Projection Brigade, corps, and division. This is consistent with Army doctrine wherein each ACE will have a team for each of the three primary intelligence disciplines. The CHACE and CHSO/TFCICA at each echelon will have to coordinate their actions closely and work as a team. The CHACE will require a robust staff of CI and HUMINT officers and soldiers to perform the following:
(c) MI Units. The CI/HUMINT XXI concept will require MI commanders and their staffs to have robust CI/HUMINT training and utilization programs to assure readiness of CI/HUMINT personnel. MI units will exercise asset management and operational oversight of assigned and attached CI/HUMINT elements.
(d) CI/HUMINT Section HQ. A CI/HUMINT Section will consist of a Section HQ, at least one Operational Management Team and at least two Operational Teams (OT). The Section HQ will consist of a senior warrant officer Section Chief and an E7 Section NCOIC. The Section HQ provides administrative, training, and operational direction (technical control and steerage) to the subordinate OMT and OTs, and may also function as an OMT when required.
(e) Operational Management Team(OMT). OMTs will consist of a warrant officer W1/W2 and a NCO E6. When tasked, each OMT will be capable of plugging into the Analysis Control Team (ACT) at any tactical brigade or battalion; the ACE at division, corps, MACOM, Army Component, or joint or combined element; the G2/S2 of any division, corps or MACOM major subordinate unit - i.e. separate battalion or brigade, or Rear Area Opns Center - or simply working out of the MI unit when CI/HUMINT assets are in a general support (GS) role. The OMT will be a self-contained operational and technical control and analysis element with at least one subordinate CI/HUMINT Operational Team (OT). An OMT will be capable of directing up to three subordinate OTs. If an operation requires more than three OTs, another OMT will be added for each set of three additional OTs or fraction thereof. The additional OMTs may merge with the original OMT to control collection and conduct analysis or they may deploy separately as the situation demands. Subordinate OTs will report to the OMT only. After conducting CI/HUMINT Single-Source analysis, the OMT will provide reporting to the supported unit, supporting ACE or ACT, and appropriate MI units. Each OMT will have the capability to:
(f) CI/HUMINT Operational Teams(OT). OT consist of one Staff Sergeant and six CI/HUMINT soldiers. An OT always operates subordinate to an Operational Management Team (OMT). It will have the capability to perform the following CI/HUMINT collection and investigation functions:
(7) While CI/HUMINT team functions will be similar and inter-operable between echelons, operational level CI/HUMINT assets may bring a regionally focused, detailed, and sophisticated CI/HUMINT capability to the lower echelon. A Long Range Surveillance force projection package consisting of 4-6 LRS teams and a command, control and communications cell should also be a piece of the CI/HUMINT Force Projection Package giving the Force Protection JTF commander and organic tactical and operational long range surveillance capability. The operational level, or Force Projection Brigade, will serve as the conduit facilitating strategic Army CI/HUMINT and national-level CI and HUMINT into the theater. As such, the Force Projection Brigade will fulfill a role commonly referred to as G2X (or J2X for the joint environment).
(a) The G2X/J2X concept will readily adapt to Army application in CI/HUMINT XXI. The G2X/J2X is the principal CI/HUMINT staff officer and controlling authority for the Army Component or joint commander. The G2X/J2X will be a senior field grade officer assigned to the Force Projection Brigade and essentially join the Army Component, corps, or division DCSINT or G2 staff as required by the situation and theater structure. The Army Component, corps or division CHSO will serve subordinate to the G2X/J2X as the TFCICA and coordinate all subordinate Army CI and joint CI activities and operations.
(b) Inherent to the G2X/J2X is area/discipline expertise, connectivity, and mission management functionality for the full range of CI and HUMINT operations. The CHSO/TFCICA will be absorbed into the G2X/J2X. The CHACE will remain in the ACE, but must maintain close ties to the G2X/J2X. This close coordination will be necessary for planning, requirements and mission management, quality control of operations, analysis, and reporting. The G2X/J2X augmentation team could include the following representatives to leverage the full capabilities of theater, strategic, and national CI/HUMINT:
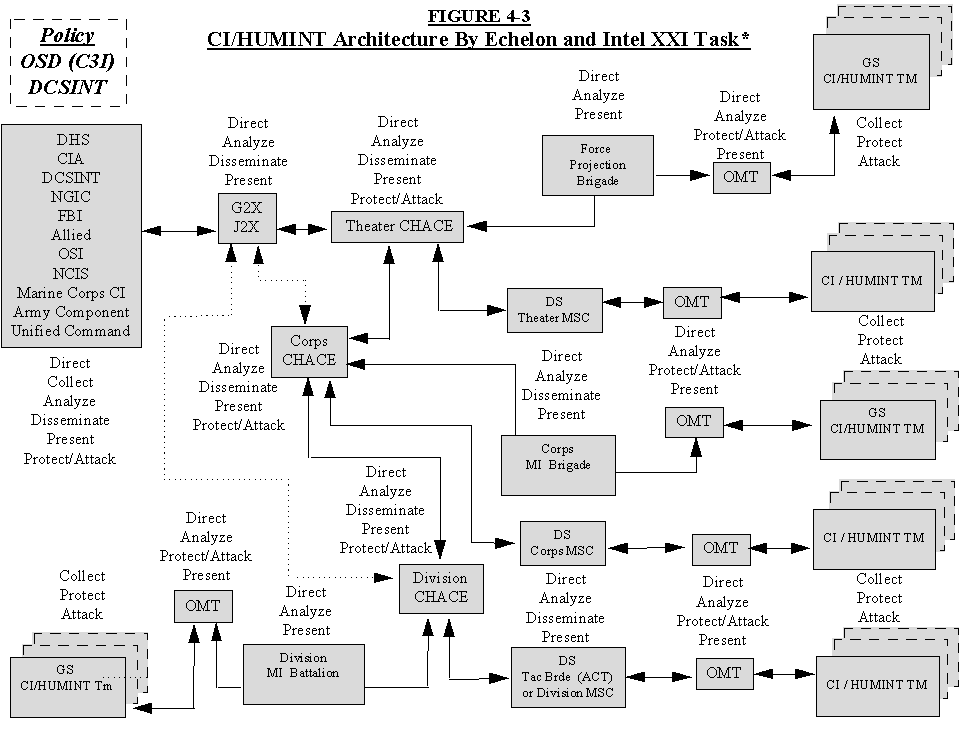
(8) Strategic CI Organizations. These organizations will perform CI investigations, collection, analysis, operations, and security countermeasures in support of strategic and departmental (TITLE X) requirements globally. They will be structured to perform the following:
(a) Mission management and planning; coordination and execution of CI mission requirements for CI projects, RED TEAM Simulations, TVAs, technical CI missions, deployments, and CI support to OPSEC.
(b) Coordinate collection efforts from all reporting elements and perform CI/HUMINT Single-Source analysis.
(c) Orchestrate Army investigations and perform quality control over Army investigations as the Army central point of contact for CI/CE investigations. This is a DA DCSINT function.
(d) Perform DIA-directed CI production. Maintain data bases on potential adversary intelligence services and produce assessments on adversary intelligence service activities. Conduct CHIPB and CI All-Source Analysis for deployed and sustaining base operations, and Army systems development and acquisition programs. Provide C2W Protect and operational analysis in direct support of strategic CI/CE investigations and special operations.
(e) Perform CI briefings, CI surveys, investigations, vulnerability assessments, liaison, and CI Special operations; detect, locate, identify, process, track, report, counteract, and exploit the foreign intelligence collection threats against friendly forces; and detect, locate, identify, process, track, counteract, and exploit deliberate security compromises by Army personnel or penetrations by FISS activities.
(f) Plan, conduct, and manage computer-related investigations, media forensics and analysis, and computer collection and operations; perform CI special operations, TSCM, and polygraph.
(g) Provide task-organized capabilities in modular team packages reinforcing Force Projection Brigades and joint/combined task forces. Teams capabilities will include collection operations, investigations and investigative case control, CI analysis, TSCM, polygraph, and computer counterespionage.
c. Soldiers. CI/HUMINT XXI functions as identified in the CONOPS can be categorized as either analysis or collection. Analysis functions parallel those of the Intelligence Analyst (96B), supporting our recommendation that we divest MOS 97G to MOS 96B. Respective CI/HUMINT collection functions are complementary in scope and purpose and, we believe, support efforts to consolidate separate enlisted and warrant officer CI/HUMINT MOSs into single specialties.
(1) There is no difference, speaking strictly of analytical functions, between the MDCI analytical function and the All-Source Intelligence analytical function. The difference is in enabling knowledge and focus. The majority of those spaces currently identified as 97G should be recoded 96B with the remainder going to 97B. They must be retained as separate analyst spaces since the all-source CI analytical function is critical to CHIPB and to CI/HUMINT collection management. The 96B Course program of instruction should include training enabling 96B soldiers to perform all-source CI analysis. We must emphasize that merging 97G into 96B will only be beneficial if the MDCI analyst spaces currently in place are not reduced and receive the same priority for fill as other 96B positions.
(2) CI/HUMINT collection functions likewise promise consolidation efficiencies. We recommend combining enlisted specialties 97B and 97E into a single specialty (97X); and warrant officer specialties 351B and 351E into a single specialty (351X). 97X and 351X should be both language and non-language required. The approximately 40% of 97B positions currently coded for language would remain so. All of the current 97E positions are language required and would remain so. This would mean that of a combined strength of approximately 2250 CI/HUMINT enlisted soldiers (750+ 97E and 1500+ 97B), approximately 1300 would be language coded. Despite potential technology applications, we see a clear need for linguists in HUMINT collection.
(3) By concentrating Division level CI/HUMINT assets at the GS Company, grade structure will be increased. This will allow for senior NCO positions in the CI/HUMINT element and will have a positive impact on operations and retention. Operations will be improved by having E7 positions in the CI/HUMINT Section, an experience level certain to improve training. Retention will be improved by the career progression this will provide to the CI/HUMINT soldier. Current CI/HUMINT team assignments to the DS Companies require CI/HUMINT leaders no senior than E6 (97B). This impacts negatively on both operations and retention. Standard CI/HUMINT team structures through the echelons (i.e.- CI/HUMINT Section with subordinate OMT and OTs) helps redress the current grade structure imbalance between EAC, which has an excessive number of senior NCO positions, and ECB, which
has a deficiency in senior NCO positions.
d. Training. The training of the CI/HUMINT soldier must be intensive and progressive. It must incorporate the latest automation/communications to bring multi-media and even virtual reality capabilities to the training site. It must be versatile--supporting both the individual soldier in a billets and thirty soldiers in a classroom.
(1) Entry level CI/HUMINT training should emphasize interpersonal skills in interview and interrogations, as well as document exploitation debriefings, elicitation, source operational cycle, and investigations functions within the OT charter. It should include training the soldier to understand the Intelligence Battlefield Functional Area, the ASAS, the CHATS and the CHASIS. Soldiers should receive instruction detailing both US and threat doctrine, tactics and capabilities/vulnerabilities. Training facilities should offer the latest technology in multi-media, virtual reality and computer assisted training to provide intensive interpersonal training without increasing instructor contact.
(2) In-unit training should enhance the skills received in entry level training and provide battle focus by preparing the CI/HUMINT soldier to operate in specific contingencies. Training facilities should ensure digital network connectivity with the Intelligence School and other MI units and organizations. Units need HUMINT and language training involving realistic simulations and distance role playing, live environment opportunities both in-country and via the Internet, document exploitation, and open source intelligence collection.
(3) Basic NCO Training should prepare the soldier to be a CHACE Team member, an OT Team Leader, or an OMT team NCO by enhancing CI/HUMINT skills with in-depth training in source operations and investigations, CHIPB, and leadership.
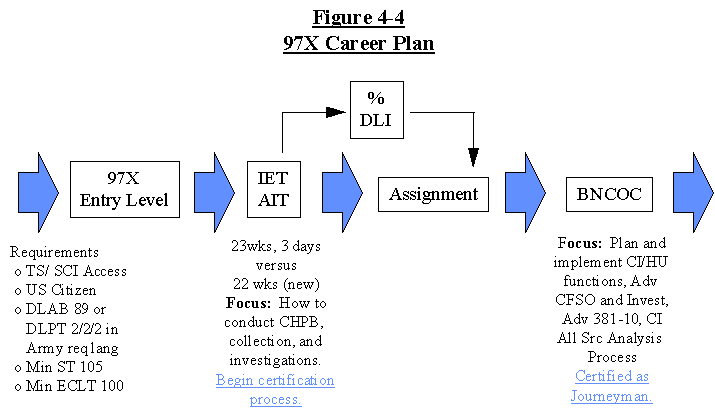
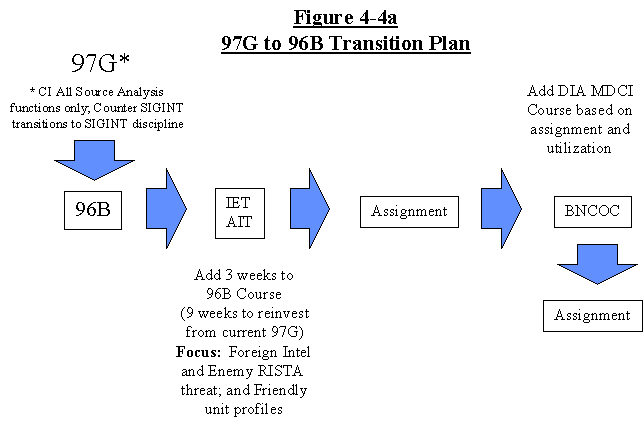
(4) Advanced NCO Training should prepare the soldier to be a CI/HUMINT Section NCOIC or Platoon Sergeant by training the fusion of all-source intelligence and the planning, directing and implementation of CI/HUMINT in Joint and/or Combined operations.
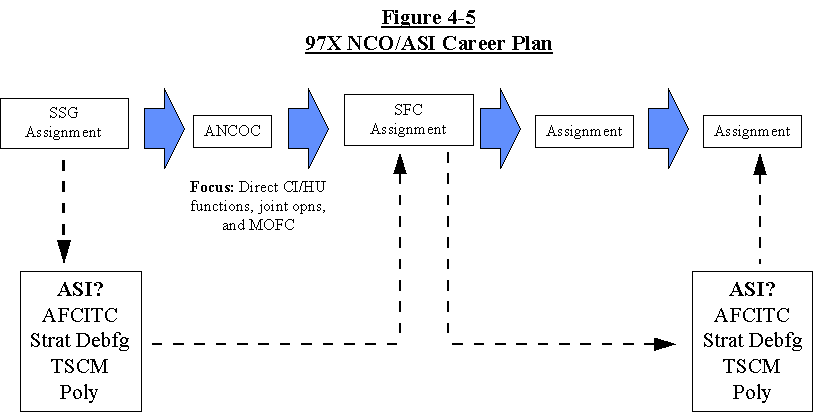
(5) CI/HUMINT Track of Warrant Officer Basic Course should prepare newly appointed warrant officers to be OMT Team Chiefs and CHACE team members by training exploitation of high level sources, the management of CI/HUMINT collection, and enhanced CHIPB.
(6) Warrant Officer Advanced Training should prepare warrant officers to be CI/HUMINT Section Chiefs by training all-source intelligence fusion and the planning of Joint/Combined CI/HUMINT operations.
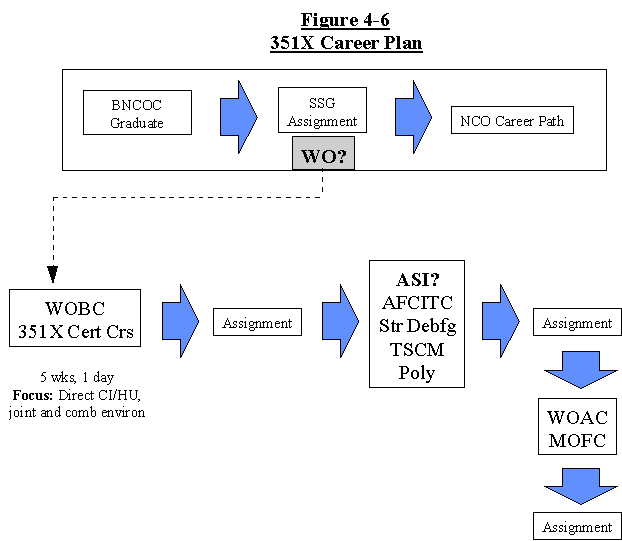
(7) Officer Assignment Specific Training (AST) for the Counterintelligence MOS (35E) should prepare 35E to be CI/HUMINT Staff Officers, CHACE OICs, and Commanders of CI/HUMINT units. It should include significantly more HUMINT, CHIPB and CI/HUMINT collection management. It should also be geared to the changing environment and incorporate lessons learned from CI/HUMINT support to ongoing operations.
(8) Certification Program We also recommend the creation of a certification program which starts upon graduation from initial entry training (IET). Battalion Commanders will certify soldiers at the basic level upon demonstration of specific skills. After completion of selected courses (e.g., BNCOC and CFSO) and demonstration of additional skills Brigade or Group Commanders may certify soldiers as a Journeyman. We expect a senior E-6 or WO1 to be certified as a Journeyman. With additional training and experience, Brigade Commanders in conjunction with USAIC&FH concurrence will designate individuals as a Master Operator. To attain the Master Operator certification, the individual must demonstrate specific skills, completed advance training (e.g., AFCITC and/or MOTC) and successfully served in specific departmental level assignments. We recommend that Officer MOS 35E have a similar certification program prior to serving as a commander in a CI/HUMINT organization.
e. Leader Development. Warfighters, MI Commanders, and other MI officers and NCOs all require a firm grasp of CI/HUMINT operations.
(1) The MI proponent should introduce CI/HUMINT XXI to battle commanders in their respective advanced courses and establish or expand CI/HUMINT instruction in the CGSOC and the CAS3 courses. Concurrently, we must teach all MI leaders CI/HUMINT XXI doctrine in the MI Officer Basic Course, MI Officer Advanced Course, the Pre-Command Course, Basic NCO Course, Advanced NCO Course, and the Warrant Officer Basic and Advanced Courses. At a minimum, topics of instruction should include:
a) The JTF and GCC Commanderís role in driving CI/HUMINT
b) How different agencies contribute to the CI/HUMINT picture--e.g. national agencies with CI/HUMINT capabilities and charters; US agencies with information of CI/HUMINT interest; non-governmental, private volunteer, and host nation organizations.
c) Leveraging CI/HUMINT in MRC and SASO
d) Army CI/HUMINT capabilities and limitations
e) Long Range Surveillance Unit characteristics, capabilities and limitations
(2) The MI proponent should ensure that realistic CI/HUMINT play is incorporated into NTC, JRTC, BTCP and all INTEL XXI simulations and exercises.
(3) We should better disseminate new CI/HUMINT concepts in MI professional journals, as well as journals of other branches.
f. Materiel. To meet Army XXI requirements and expectations, CI/HUMINT will have to leverage capabilities across echelons, military services and operating environments. This will require a common CI/HUMINT set of automation and communications hardware and software, compatible with both the All-Source Analysis System (ASAS) and the DoD CI Integrated Information System (DCIIS). These systems and associated tools will bring with them common reporting fields and databases, digital photography and video collection and presentation, document translation and open source intelligence exploitation capabilities, single-source analysis and collection management tools, and a set of CI and counter-RISTA (reconnaissance, intelligence, surveillance, and target acquisition) analytical tools.
(1) A key objective of CI/HUMINT XXI will be to have like and compatible equipment across echelons, especially at the tactical and operational levels. We will have to give CI/HUMINT assets and entities the capability to move and communicate across the battlefield during split-based, force projection operations. The greatest materiel requirement is to provide teams with automation and communications equipment capable of operating in the ASAS and DCIIS environment.
(2) CI/HUMINT will requires three tiers of automation and communications materiel support.
(a) Tier I - CI/HUMINT teams require equipment facilitating common Army and joint reporting, database manipulation, digital photography and video usage, collection tasking and source analysis operations, and rapid analysis of CI/HUMINT information relative to CHIPB and the all-source picture.
(b) Tier II - OMTs and MI unit CI/HUMINT operations elements require a CI/HUMINT remote work station that has full collection management functionality, CI and C-RISTA analysis tools, CHIPB tools, and is compatible with ASAS, DCIIS and OT equipment.
(c) Tier III - The CHACE requires a CI/HUMINT single-source workstation with full ASAS and DCIIS functionality and a free text search capability. This functionality must extend to the ACT, enabling the OMT to "plug-in" to ACT ASAS RWS in support of Brigade requirements.
(3) CI/HUMINT XXI requires robust, secure voice, data, and video communications that will be compatible with other battlefield communications devices for short, mid- and long-range communications. CI/HUMINT will also need a stand-alone communications capability for deployment in austere environments.
(4) CI/HUMINT XXI requires modernized equipment to perform the technical and specialized CI/HUMINT functions, e.g., technical surveillance, TSCM, polygraph, OSINT, and investigative and analysis tools. CI/HUMINT XXI will also require research and development initiatives to enhance capabilities, e.g., human measurements and signatures, long-range voice listening tools, foreign language translation devices, source psychological profiling tools, and source tracking tools.
(5) CI/HUMINT OTs and OMTs require two vehicles each to ensure mobility and accessibility across the battlefield and/or operating environment.
Appendix 5: Combined CI/HUMINT Operations
1. While our CONOPS addresses concepts and architectures within the US force structure, we believed comments made regarding Combined operations deserved special note. Combined operations, like Joint operations, will likely be a definitive part of our Army CI/HUMINT XXI future. Our discussion here is less prescriptive and more descriptive of those actions we must take to ensure successful Combined CI/HUMINT operations. Weíve added this appendix to serve as a resource for doctrine writers and trainers building curricula and programs addressing the full-range of CI/HUMINT operations.
2. The Combined environment is fraught with unique operational, policy, and legal challenges and opportunities. The challenge facing CI/HUMINT officers is capitalizing on the opportunities while reducing the friction posed by challenges.
3. Combined CI is unique by definition since counterintelligence remains a national responsibility in most circumstances. Consequently, each participating nation brings with it a different set of rules and operational doctrine. This is further complicated by wide differences in legal and operational authority granted by nations to their CI forces. Add to this a nationís desire to protect its methods and sources and the stage is set for bedlam. Cultural issues can also play a significant role in Combined operations. The best recent example of this cultural impact was the need to have Russians as part of IFOR because Slavic Serbs were not willing to trust the actions of other, possibly biased, NATO countries. These and other operational issues can be overcome with detailed prior planning that involves as many of the participants as possible.
3. One operational issue which must be resolved prior to deployment is that of intelligence, information, and communications architectures. The issue is paramount not only because of operational concerns, but because of the divergent perspective each nation brings to the operation. Traditional US architectures broadcast information and intelligence freely throughout the battlespace in an effort to attain information dominance and ensure commanders have what they need to make time-sensitive decisions. Other nations may use a sequential approach to dissemination in order to tightly control the release of information. In every operation, CI information must be fused with information from other disciplines to establish a common relevant picture of the battlespace and threat. This concept remains a distant goal for many nations confining their reporting to a vertical stovepipe system. Achieving effective information flow is difficult in the Joint environment; the challenge increases exponentially in the Combined environment.
4. Combined CI operations must be well planned, well coordinated, and efficiently executed. For this to happen, a single coordinating point must be established in the controlling headquarters intelligence section. Within Joint doctrine, this focal point is the Joint Task Force Counterintelligence Coordinating Authority. This concept may be alien to many contributing nations. It is therefore critical that US forces participating in combined CI operations emphasize the need for the single coordinating focal point within the senior controlling headquarters.
5. CI operations vary in execution due to differences ranging from METT-T to participating nation interests. Generally, however, operations will assume some form between the national zone approach (the simplest), and the truly combined, fully integrated approach.
a. The national zone approach is operationally simplest because it divides the AOR into zones and assigns one or more to each contributing nation. Within their zone, nations conduct CI operations in support of controlling headquarters requirements employing their own national CI doctrine. This approach precludes many of the problems associated with integration as nations operate within their spheres of experience and focus upon gaining information--not protecting their collection methodology.
b. The fully integrated approach is much more difficult because it combines CI forces from different contributing nations into one force. This format compels participating nations to determine the degree to which they will share information and methodology, exacerbates differences in reporting procedures, and complicates efforts to ensure compatibility in equipment and communications architectures. Invariably, participating nations will come to agreement on the degree to which they will integrate and the relative cost to be shouldered by each.
Appendix 6: CI/HUMINT Outsourcing Candidates
1. Our outsourcing recommendations focus on those functions not required in a combat area and are based upon our assessment that their divestiture would achieve real cost savings.
a. Personnel Security Investigations (PSI). We have not included PSI as a CI/HUMINT XXI function at any echelon or in any environment. This will continue to be a Defense Investigative Service (DIS) mission. If they are unable to accomplish the mission in CONUS and/or OCONUS, then we recommend they use contractors.
b. TEMPEST. Though a TEMPEST threat exists (OCONUS), we have not included TEMPEST as a CI/HUMINT XXI function at any echelon or in any environment. We believe that through better education and an aggressive physical security program, we can minimize the threatís capability to collect information from electromagnetic signatures. Due to the minimal threat in CONUS, NSA and other DoD agencies have decreased resources to TEMPEST programs. NSA no longer publishes the list of acceptable electronic/ADP equipment meeting NSA TEMPEST standards. NSA places greater emphasis on the installation and zone security. NSA only conducts TEMPEST tests of equipment in special cases. The Army must adopt similar policies and look to NSA or contractors for specialized TEMPEST support.
c. Polygraph. Outsourcing polygraph is not practical due to legal and policy conflicts. Currently both CID and CI agents conduct polygraph tests for the Army. However, the purpose of the examinations are different - one criminal, the other intelligence - and the procedures for conducting them are also significantly different - CI uses different questioning methods. Based on the uniqueness of each mission and the continued critical need for polygraph support to intelligence and source operations, it is not practical nor feasible to combine CID and CI polygraph functions. Prior to a final decision, Army needs to study the feasibility of using FBI and CIA examiners.
d. TSCM. This is a valid function in deployed areas of operation and we need to keep enough TSCM trained Army CI agents to perform this critical service for deployed commanders. It is possible that we could contract out TSCM detection and inspection services in a non-conflict situation. However, once a device is identified, then the operation becomes an issue requiring an investigation by a qualified CI agent. At the very least, a mix of Army civilian and military personnel would meet the TSCM needs for Army XXI.
e. Language Support. This is an excellent candidate for outsourcing. Even if we continue to train linguists and maintain our 97L Linguist Pool, we will still need to contract linguists for most future operations to get the right amount and mix.
f. OSINT. This is a good candidate for contracting, and has proven to be a valuable function during recent operations in Haiti and Bosnia. The Lukavac Night Owl, a daily open source production in Bosnia, employed eight local nationals hired by BDM to translate local newspapers, radio, and television. These local nationals were supervised by active duty linguists. Improvements in connectivity will permit collaboration with academia, private industry, allies, and other government sources to provide additional open source exploitation and analysis.
g. Technology Protection Programs. Protecting the force begins with the protection of our technology. Assuring the survivability of battlefield equipment enhances force protection and increases our combat effectiveness. We cannot decrease the emphasis on technology protection programs. However, significant strategic/operational CI resources are dedicated to protecting sensitive technology. While we cannot eliminate the commitment of Army assets, there is potential to reinvest some resources committed to technology protection to other critical strategic/operational requirements. This area requires a major review to determine the right mix of Army resources and contractor support.
h. CI support to DoD Intelligence Systems Security Site Based Accreditation and SCI Contractors. This area is an exceptional candidate for outsourcing. It is a CONUS-based requirement to support contractors with security manager and countermeasure expertise. This expertise is available through other sources.
i. Telecommunications Monitoring. This is a viable function. However, it requires additional money, training, equipment, and personnel inconsistent with traditional CI/HUMINT organizations and equipment. NSA, LIWA, Army SIGINT are the best candidates to perform this function after appropriate legal and policy changes.