Air Force
Air Force Intelligence and Security Doctrine
 Air Force
Air Force Security
INFORMATION SECURITY
H This directive provides Air Force policy for protecting sensitive Air Force information. It also assigns responsibility for implementing and managing the Information Security Program. This directive implements national policies in the Executive Order 12356, National Security Information, 2 April 1982, and Information Security Oversight Office Directive 1, National Security Information, 22 June 1982. It implements DoD 5200.1-R, Information Security Program Regulation, June 1986 and interfaces with various other security publications such as AFPD 31-5, Air Force Personnel Security Program; AFPD 31-6, Air Force Industrial Security Program; AFR 205-43, Safeguarding NATO Classified Information; and AFI 31-401, Information Security Program Management (formerly included in DoD 5200.1-R/AFR 205-1). Policy for classified information designated Sensitive Compartmented Information is managed under the provisions of Director, Central Intelligence Directive 1/19, Security Policy for Sensitive Compartmented Information, 19 February 1987, and USAFINTEL 201-1, The Security, Use, and Documentation of Sensitive Compartmented Information (SCI), 1 May 1990. (Copies of these publications are available from the supporting Special Security Office.)
SUMMARY OF REVISIONS
This revision clarifies the purpose, the policy, the responsibilities of commanders, and the reporting requirements for metric data. A H denotes a revision from the previous edition.
H 1. Air Force personnel must protect classified information from compromise by proper classification and safeguarding.
2. The Office of the Secretary of the Air Force (SAF/AA) is designated the Air Force Senior Security Official responsible for ensuring implementation of the Information Security Program.
3. The Air Force Chief of Security Police (HQ USAF/SP) is responsible for policy, resource advocacy, and oversight of this program.
H 4. Commanders of major commands (MAJCOM) and installations are responsible for establishing Information Security Programs, identifying requirements, and executing their programs to comply with this policy.
H 5. The senior security police official at each command, direct reporting unit, field operating agency (FOA), or installation is designated the Information Security Program Manager (ISPM). Commanders appoint an ISPM at locations without a senior security police official. ISPMs manage Information Security Program implementation and provide oversight within their commands.
6. Each unit commander or staff agency chief will appoint a security manager to manage the Information Security Program. Appointing officials will ensure security managers receive required training.
7. Compliance with these policies is mandatory for all Air Force military and civilian personnel.
8. See attachment 1 for ways to measure compliance with this policy.
H A1.2. MAJCOMs and direct reporting units will submit a report semiannually to HQ USAF/SPI by 31 January and 31 July of each year. The same requirement applies to FOAs except they must submit their report through their respective air staff or secretariat office. All will report on
H A1.5. Reporting activities are encouraged to provide their ideas on how to improve the measurement method.
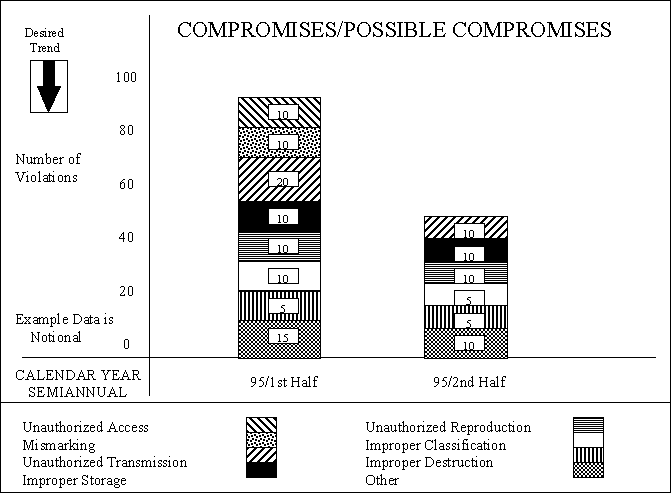
Figure A1.1. Sample Metric of Compromises/Possible Compromises by Type.