
[Back]

[Index]

[Next]
AIR FORCE PAMPHLET 14- 210 Intelligence
1 FEBRUARY 1998
 [Back] |
 [Index] |
 [Next] | USAF INTELLIGENCE TARGETING GUIDE AIR FORCE PAMPHLET 14- 210 Intelligence 1 FEBRUARY 1998 |
2.1.1. Sources of Information. Information can take many forms and be derived from many sources. Information can result from observing or reporting an event. It can be derived from the manipulation of facts through computation. It can also result from professional opinions, judgments, and interpre-tations by participants. Information may be objective or subjective. Usually, it comes from a combi-nation of sources and is a presentation of both fact and insight.
2.1.2. Characteristics of Information. Information has many characteristics and does not come without cost. Acquiring sufficient, accurate, and timely information can be very expensive. It can be perishable and is generally imperfect. Consequently, information from one source should be verified with another source whenever possible. Frequently, information derived from one source can be used as a cue in researching other sources or in collecting additional or different information. Information can be acquired through various methods. Each has advantages, and all have inherent and environ-mental limitations and constraints. The observer, as a source of information, is often biased. Observ-ers are also limited by what can be seen. Since it is difficult to observe an elaborate and dynamic system, the tendency is to "freeze" the situation and examine individual system parts in a static state. In doing so, essential ingredients are frequently lost. There is often the danger of attributing a great degree of precision to imperfect assessments or measurements. Because of these many limitations, information varies in validity and reliability.
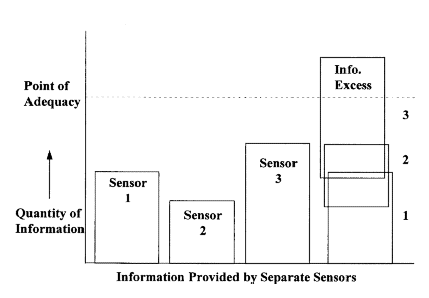
2.1.3. Information Threshold. The information threshold is that point in time when one has accu-mulated enough information to make a valid decision. In theory, one should keep collecting informa-tion until the information threshold or the point of adequacy is reached. As figure 2.1 suggests, independent information sources 1, 2, and 3 do not provide sufficient information to reach the thresh-old. But when information from all three sources is combined, the threshold is reached and the point of diminishing returns (that is, when the additional information costs more to collect than the value gained from having it) is reached. Keep in mind that the point of adequacy for information is adjust-able depending on the fidelity of information needed. If the various portions are viewed as an "infor-mation budget", the information threshold and collection resources can be managed accordingly. 20
2.1.4. Intelligence Processing. Since information does not present itself for exploitation, it must be sought, gathered, assembled, and processed into usable form. The outcome is the transformation of raw information into intelligence suitable for making valid decisions. There are three levels of intel-ligence support: strategic, operational, and tactical. Strategic intelligence is required for the formula-tion of strategy, policy, and military plans and operations at national and theater levels. Operational intelligence is required for planning and conducting campaigns and major operations to accomplish objectives within theaters or areas of operations. Tactical intelligence is required for planning and conducting tactical operations. Intelligence sources are the means or systems used to observe, sense and record, or convey information. There are seven primary intelligence source types: imagery, human, signals, measurement and signature, open source, technical, and counterintelligence.
2.1.5. The Intelligence Cycle. As stated in JP 1- 02, the intelligence cycle is defined as "the steps by which information is converted into intelligence and made available to users". The five steps in the cycle are:
2.2. The Fusion Principle. 2.2.1. Fusion. The process of combining multisource data into intelligence necessary for decision making is called fusion. Due to the limitations inherent in any collection system, and because other countries strive to misinform or deny information to intelligence gathering agencies, intelligence nor-mally should not be based on single source data. Intelligence becomes more useful and more reliable when information from all possible sources is collected, combined, evaluated, and analyzed in a timely manner.
2.2.2. Accuracy and Timeliness. Fusion of multisource data adds credibility to intelligence esti-mates. Given the vast quantity of material collected and the rapid pace of modern warfare, the fusion process should be automated whenever possible and its products made readily available to all levels of command. Fusion facilitates accuracy. Accuracy and timeliness should be a constant goal of all tar-geting personnel.
2.2.3. Application of Fusion. Fusion is not always possible, but the principle should be used when-ever possible to enhance intelligence support without degrading the timeliness of that support. There are times when information from one source cannot be confirmed by others or is highly perishable. Factual and important single source information should be disseminated immediately. Follow- on data should be presented when it becomes available.
2.2.4. Organizational Structure. Organizational structure can aid both the fusion process and the flow of useful intelligence. Effective staff structuring, coordination, and cooperation are imperative if the commander's intelligence needs are to be met.
2.3. Hierarchy of Intelligence Products. Intelligence production and fusion can also be viewed through a hierarchy of products. There are five categories in intelligence production, with each one a building block. They are: raw or unevaluated data; processed data; analyzed basic data reports; integrated intelli-gence; and intelligence end products. Through fusion, improved products are built from those lower in the hierarchy.
2.3.1. Raw or Unevaluated Data. This is the basic building block from which all intelligence prod-ucts are derived. It includes unexploited film from reconnaissance missions, untranslated messages from intercepted communications, recordings of foreign radar signals, and all other types of raw data.
2.3.2. Processed Data. The second level in the hierarchy is made up of materials that have been refined to a stage where they can be analyzed. This can include initial imagery interpretation reports, translation of captured documents, and preliminary reports based on intercepts of foreign radar sig-nals. This data is produced by agencies such as imagery interpretation facilities, human intelligence (HUMINT) detachments, and electronic reconnaissance processing elements. The Contingency Air- 22
2.3.3. Analyzed Basic Data Reports. At this level of the hierarchy, intelligence products from simi-lar sources are compared and collated, but there is no attempt to fuse intelligence from these sources. For example, all imagery interpretation reports on a single installation may be collated, or translated message traffic from two foreign army units may be compared. Basic data reports are used to form a data base and result from a collation process oriented toward individual weapon systems, installations, or types of material.
2.3.4. Integrated Intelligence. These products result from detailed analysis and fusion of multiple intelligence sources. Examples include orders of battle, scientific and technical reports, intelligence estimates of foreign power capabilities and intentions, and the installation and orders of battle data in the MIDB. Integrated intelligence is usually produced at Joint Intelligence Centers (JIC) and by the national intelligence community. DIA, Unified Commands, the Central Intelligence Agency (CIA), and the National Security Agency (NSA) are all major producers. Integrated intelligence products are, in turn, used to produce other intelligence products.
2.3.5. Intelligence Products. This category includes materials intended for dissemination to users. End products result from additional analysis, evaluation, and fusion of materials produced at lower levels in the hierarchy. These products are probably the most important, and when available are the best source on which to base force employment decisions. Electronic versions are available through INTELINK and SIPRNET. Newer information technology now allows links between intelligence producers. The Air Force Information Warfare Center's (AFIWC) SENSOR HARVEST is an exam-ple.
2.4. Prerequisite Information and Intelligence for Targeting. To begin target planning the following information requirements should be addressed to prevent waste of resources.
2.4.1. Intelligence on Enemy Defensive and Offensive Posture, Capabilities, and I nt e nt i ons . The targeteer must have current, accurate intelligence on the enemy's status and predisposition.
2.4.2. Target System, Component, and Element Characteristics. Targeteers must have current, accurate intelligence on the physical, functional, mobility, and environmental characteristics of poten-tial enemy targets.
2.4.3. Friendly Force Posture and Capabilities. The targeteer should know what forces will be available for offensive operations and the capabilities of these forces. Care must be taken to prevent potential options from being overlooked because a capability is assumed not to be available. If a force capability not available at the beginning of an analysis can be demonstrated to be clearly superior, it may be possible to obtain the capability. In any event, targeting personnel should be aware of current and potential force capabilities and consider them during their analysis.
2.4.4. Concept of Operations, Mission Objectives, and Rules of Engagement. The targeteer must understand the concept of operations and mission objectives in order to conduct an analysis that results in target recommendations to achieve those objectives. They should remember that most offensive operations take place in a joint service environment. Consequently, the scheme of maneu-ver of other component forces should be known to make all systems effective, and the operation of the USAF component should be integrated as much as possible with them. Even though the Unified com- 23
2.4.4.1. For targeteers to function effectively, they must understand Air Force and Joint doctrine. Doctrine is important because it is based on the capabilities of the US military and states funda-mental concepts upon which planning should be based.
2.4.4.2. Another prerequisite for target analysis is a general knowledge and understanding of the tactics that will probably be employed during actual operations. Specific operational restrictions must also be considered. These may consist of international law limitations, rules of engagement (ROE), area closures because of operations, or restrictions laid down by commanders or foreign governments.
2.4.4.3. Targeteers must also be able to perform analysis that could lead to policy changes, such as a lifting of certain ROEs. The ROE can be changed, but this rarely occurs unless higher author-ities are made aware of a requirement for a change. The effects of such restrictions can and must be clearly stated to the commander so action can be taken to change them.
2.4.5. Time Constraints. Time is a critical commodity and must be managed skillfully. The targe-teer must have the right information in time to assist the decision maker.
2.4. 5.1. The response time for providing support varies with each of the categories of missions identified in ACCI 13, Air Operations Center, Volume 3. Preplanned missions are those for which a requirement can be foreseen, permitting detailed planning and coordination. Immediate mis-sions are those for which specific target makeup and location cannot be determined in advance.
2.4.5.2. The six functions of the strike or attack mission cycle are performed for both preplanned and immediate missions. The entire cycle may take from seconds to weeks, and targeteers must be responsive to the time requirements of this cycle. Rapid decision making is essential for immedi-ate mission support. If targeteers cannot provide timely support to the commander, they are likely to be ignored in future decision making. Locating those analysts close to the decision makers can increase responsiveness. The targeting process must be made to fit within the decision cycle where appropriate. For instance, not all immediate attack cycles need targeting support, if that support is not value added to the decision.
Foot Stomper Box
Doctrine is even more important than a planner might initially think. JCS and the Commands use a com-plex,
but well documented, Deliberate Planning Process to construct and update Operations and Concept
Plans. In the fast breaking crisis environment of world media attention, these procedures are pared down
to Crisis Action Planning. The deliberate and iterative process of what the nation needs to effect and what
it wants the new enemy to do is often lost to what the various agencies, services, and commands can do.
Doctrine is still more important when faced with unclear, or still forming, objectives and guidance. The
targeteer must help formulate objectives and guidance. Knowledge of interdiction (JP 3- 03) or C3CM (JP
3- 13) provides a solid basis for good planning.
24
2.5.1.1. The objective of the CM process is to satisfy the commander's essential elements of infor-mation (EEIs). These are necessary to accomplish the given mission and assigned operational tasks. The collection manager is a central figure of the process, serving to coordinate and facilitate the activities of two cyclic, mutually supporting functions: the translation and development of taskings, referred to as Collection Requirement Management (CRM), and the employment of intelligence collection resources, known as Collection Operations Management (COM). The two functions are structured to support the operational commander's mission statement in a responsive manner (figure 2.2).
Foot Stomper Box
There was argument during and after the Gulf War about Intelligence support to the "Black Hole" at CEN-TAF.
Part of the problem evolved from space constraints, which kept targeteers away from the decision
makers. Also, the split of the planning functions into two different offices (" Black Hole" and TACC's
Combat Plans) led to lack of timely support because of scarce resources. However, the Summary Report
of the Gulf War Air Power Survey, (p. 128), states "Various planning documents written before the war
outlined the organizational relationships that would exist between intelligence analysts, targeteers, and op-erations
planners. Those that developed during Desert Shield and Desert Storm differed considerably from
what had been envisioned." In short, we didn't follow our own doctrine.
25
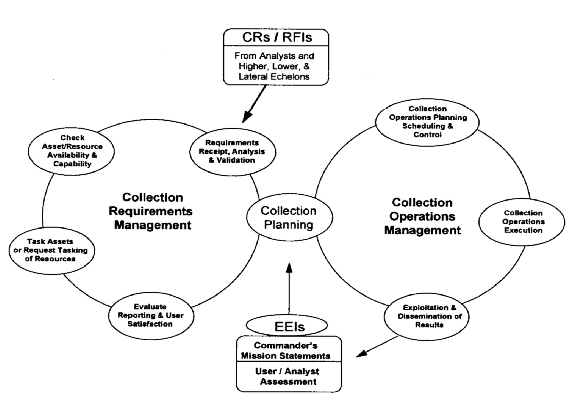
2. 5. 1. 3. COM facilitates the execution of the collection tasking and mission guidance that was developed to satisfy the validated collection requirements and RFIs. It is dependent upon those supporting organizations and other units or agencies that own and operate the collection assets. COM consists of the following tasks: planning and scheduling of collection operations; execution and control of collection operations; exploitation and dissemination of the resultant intelligence products. With respect to COM, the collection manager is usually supported by one or more col-lection operations managers. They are members of the unit's operations staff or who reside with other units or agencies that actually own and operate the collection assets. Although it is possible for a collection manager to be responsible for performing COM, the function is usually executed 26
2.5.1.4. Collection Requirements . Always state intelligence requests clearly and include pre-cise parameters (desired and minimum required) and a written statement of justification. Parame-ters should include suspense dates, frequency of coverage, resolution/ level of information, and specific viewing angles/ direction (IMINT).
2.5.1.4.1. Requirement Identification . Targeteers must ensure collection operations man-agers are aware of targeting objectives, information needs (quality, quantity, frequency, etc.), and the constraints and limitations imposed on the targeting process. This includes informing the collection manager as soon as possible of tasked targets. The information must include the type and number of desired munitions, in addition to the desired effect.
2.5.1.4.2. Collection Priorities . The value of targets may change during crisis or conflict, and the targeteer must update the collection manager so collection priorities can be adjusted, if needed. Requirements and their associated priorities need to be established for peacetime tar-get surveillance, crisis monitoring, and combat support (in support of targeting, threat assess-ment, database maintenance, and damage assessment). All targets should be prioritized and monitored on a routine basis. In most cases, higher priority targets are collected with greater expediency and frequency than targets with a lower priority. Mobile targets present a specific collection problem because their data is extremely perishable and current data is essential to target analysis.
2.5.1.5. Collection Operations (Systems) . It is the collection manager's responsibility to make decisions on sensor choice, since they are responsible for managing the assets and choosing the most efficient methods and sensors to satisfy requirements. On the whole, theater sensors are more flexible and have a faster reaction time to collection requirements. National collection plat-forms are not as flexible and have set times and locations where they will be collecting on a target area. The choice of which targets will be collected by these assets, must be coincident with spe-cific national system collection ground tracks. Dissemination of national system products relies on primary and secondary dissemination methods and equipment in theater. If communication lines are insufficient enough to handle dissemination of imagery, the product will not be reactive to theater needs.
2.5.1.6. Exploitation Requirements . Targeting must also identify the essential elements of information (EEI) required from imagery and all- source analysts. There are two types of EEI -generic and specific. If generic EEIs are requested, the imagery analyst will report all activity and identify all structures on or in the target area. Generic EEIs are listed as part of the overall com-mand objectives and may vary in different commands. Specific EEIs are instructions the cus-tomer/ targeteer provides with the RFI to report specific activity/ observations (e. g., general BDA of the entire facility or a specific assessment of a critical target within the facility). 27
Foot Stomper Box
Imagery interpreters were often unaware of several factors critical to Gulf War Battle Damage Assessment.
Time- on- target, number and type of munitions, intended effects, and campaign target significance were not
passed in the vast majority of cases to the widely dispersed intelligence production organizations. Assess-ments
of BDA were quickly dismissed by operational planners early in the Gulf War. Credibility was nev-er
fully restored, and many false lessons learned and negative impressions were created. The targeteer
must do everything possible to point the collection managers to the best source for the intelligence they
need. Operational planners should remember that in war an action not assessed is still a task and will have
to be planned again.
28
 [Back] |
 [Index] |
 [Next] | USAF INTELLIGENCE TARGETING GUIDE AIR FORCE PAMPHLET 14- 210 Intelligence 1 FEBRUARY 1998 |