July 6, 2001
Technologies and Procedures to Verify
Warhead Status and Dismantlement
SIPRI Workshop, Paris, 02/08-09/2001
Richard L. Garwin
Council on Foreign Relations, New York
INTRODUCTION: THE LIFE STAGES OF NUCLEAR WARHEADS
In this chapter we consider how one could provide assurance of compliance with some cooperative regime limiting numbers or location of warheads. These techniques and procedures might be adequate for verification of a formal treaty, or they might serve the lesser goal of transparency, to provide some confidence in compliance with a treaty or other undertaking.
If nations continue to possess such fearsome weapons as nuclear warheads, each with the capability of destroying a good fraction of a million people, they will not take lightly to measures that may increase the vulnerability of the warheads or impair their readiness for use. On the other hand, if there are major security gains in a posture of reductions and constraints on use, nations may choose to adopt them, in the process sacrificing some flexibility in regard to their own warheads. We assume that such agreements would be more seriously considered if there were tools for providing adequate transparency. But these measures do not presume the prohibition or even the major reduction of warhead numbers in every instance. Such a regime for control and accounting is highly desirable in any case for a state's own security interests, and is a necessity if warheads are to be limited short of prohibition. Of course, if such items are prohibited rather than limited, verification becomes much simpler.
In the early years of nuclear weaponry, warheads were assembled, stored, deployed, and more of them were lost to accident (and hundreds expended in nuclear explosion testing) than the two that were used in warfare. For almost the past decade, neither Russia nor the United States has tested a nuclear weapon, although one Russian warhead at Semipalatinsk, already emplaced for test when nuclear explosion testing stopped in Kazakhstan, was destroyed by conventional means.
Over the past half century, tens of thousands of warheads have been disassembled and many of them recycled as warheads of slightly different type, or even remanufactured.
At present, warheads undergo a life cycle with manufacture from nuclear materials, transportation, storage, transportation, deployment, transportation, storage, and disassembly and remanufacture, or transformation to special nuclear material (SNM) stockpiles and storage.
In the normal course of events, warheads may be routinely remanufactured after ten years (as is reported to be the case with Russian nuclear weapons), or routinely inspected and modified as necessary.
In connection with the U.S. Stockpile Stewardship Program, much information has been released by the Department of Energy itself, and as unclassified reports of the JASON group of consultants to the U.S. government. A useful report is available also from the British nuclear weapons program.(1)
OUTSIDE THE REGIME-- COVERT WARHEADS. In outlining technologies and procedures for verification of agreed undertakings in regard to nuclear warheads, one must recall that a major concern is with warheads that have never entered the regime but in a parallel world are either statically hidden or are actively maintained and ready for use. Furthermore, new warheads might be manufactured from SNM-- most commonly plutonium or high-enriched uranium (HEU). Strict controls over stockpiles of SNM and suitable facilities for manufacturing would be needed to control this threat. Warheads are small, and even in the smaller nations there are numerous places to put 100 warheads. For instance, they could be stored in mines, in conventional armories, in the basement of high-security government buildings not otherwise related to nuclear weaponry.
If the state does not intend this diversion of nuclear warheads, then its own system of security, control, and accounting for nuclear warheads should catch the diversion; hence an interest of every state to institute as soon as possible appropriate measures to provide security, control, and accounting for its own warhead stocks. And it would be desirable to have such systems defined in a fashion that would be useful for a future transparency regime.
If the state intends a diversion, then it must keep records and also provide a limited number of individuals with information about the purpose of the covert store of nuclear weapons. Else they will be of little use and considerable hazard to the purposes of the state. It will need also to provide security, surveillance, and very likely appropriate maintenance for the covert warheads, as well as a means to bring them out and mate them with delivery vehicles.
One aid in deterring such diversion is so-called societal verification.(2) New treaties ought to make provisions for societal verification, by which the text of the treaty is published widely in the States Party, domestic law is established that makes it illegal for individuals to perform those activities that the state has agreed not to perform, and permission and responsibility are given individuals to report to the Verification Commission a state's violation of the agreement.
Societal verification will also play a role in reinforcing the effectiveness of a transparency regime dealing with warheads that have been entered into the regime.
A VERIFICATION REGIME
Much excellent work has been done on the elements of a regime for verification of an agreement limiting warheads and special nuclear material. Many such agreements can be conjectured, some of which would limit only numbers of warheads of specific types; others numbers, locations, and readiness, and the like. Even for a regime that limits only numbers, e.g., to a total of 3000, it is clear that individual warheads or amounts of fissile material need to be identified. Hence the requirement for tags and seals-- tags to show the claimed identity of the TLI, and a seal to provide assurance without great effort that the TLI is indeed present and has not been removed.
Consider regulating or even just taxing automobiles. Without identifying marks, automobiles could be counted by bringing them all to a relatively few locations and arranging them in blocks of 10, super blocks of 100, and the like, to ease counting. Then one could establish that there were no automobiles at all outside the fields on which they were massed. After the census, the automobiles could be released and brought back again in a time comparable with that for creation or destruction of an automobile.
Instead, automobiles have a tag (a license plate, typically), and a more permanent identifier on the engine block, windshield, or frame. In some states, the license plate is an official document, whereas in Britain, for instance, one can provide one's own identifier, just so that it displays clearly the number under which the vehicle is registered. The use of tags converts a limitation to a total ban-- but this time a ban on non-tagged items. With tags, no longer do all the TLI have to be brought into one place for counting. But it doesn't make a lot of sense to do an exhaustive enumeration of TLIs. Instead, some sampling approach can be used to verify the declarations. Rather than repeat what I have already published, I attach a discussion paper of 1990(3) and a publication from The Council For Arms Control of 1988.(4)
Once a nuclear warhead or package of special nuclear material (SNM) has become a TLI and has acquired a tag and a seal, the regime for verification or transparency regarding these TLIs has much in common with any other protection, control, and accounting regime. But recent developments in information technology should make the transition to such a verification and transparency regime much more acceptable than was previously the case. In my 1990 document I describe how this would work for a "battalion" ("Bn"), but it would be similar for any unit controlling a number of nuclear weapons:
"... an encrypted file (is) provided daily by each Bn
to its headquarters and communicated to the other side.
When decrypted, the lines in the table constitute a
list of the TLI with their individual identification
numbers. Each Bn (and, if desired, each line in the
table) could have a different cryptographic key, so
that there need be no valid concern about the
inspecting side being able to break the code and obtain
clear information about the details of deployment of
every one of the TLI. In fact, schemes exist by which
additional standard text is encrypted together with the
information lines of the table, and alternate bits or
characters deleted from the encrypted table, so that
the information is just not there, even if the
cryptographic key were communicated. Under these
circumstances, the information in the table would only
be available when provided in the clear by the
inspected side. The encryption would serve simply as a
means of validation of the clear text-- the test being
that the asserted clear text when encrypted by the
asserted key gives precisely the deposited cipher text.
In principle, this scheme is analogous to a perfectly
secure envelope that can be available at any time, that
cannot be forged, and that cannot be destroyed."
Nuclear weapons and SNM are dangerous and potentially valuable. A nation should want to protect, control, and account for such objects, treaty or not. So if it is possible at reasonable cost to tag and seal such items and to report currently to higher authority their identity and locations, it would have merit outside any arms limitation agreement.
In principle, each TLI would have a corresponding line in the table, and each line in the table would correspond to a TLI. There may be reasons to have dummy lines, in case a party did not want to possess the full number of warheads permitted by the agreement. Lines will contain a date and precise time, so that the encrypted version of two dummy lines will not be identical.
With each line in the table encrypted with its own key by a standard encryption algorithm such as triple-DES (digital encryption standard), there would be no hope of obtaining any information without the key. In order to verify the accuracy of the listing, an inspector might be admitted to a location of choice, where there was a warhead to be found. The host nation would then identify the line in the encrypted file belonging to that warhead and would provide the 168-bit key that would be used to decrypt the line. The line would then reveal the serial number of the tag, perhaps the serial number of the warhead itself, and the location. All of this information would have been available to the inspector already from the physical object.
The other portion of verification would be on a sampling basis to ensure that all the warheads were where they were asserted to be. This would be accomplished by picking at random a line in the table, having it revealed to indicate where the particular weapon was, and freezing that weapon in place until it could be visually inspected.
Alternatively, as indicated in the 1988 paper, the tag (or a cooperative communication system) could be used to communicate the identity and location (verified by GPS) of the object, reducing the cost and intrusion of a visit.
Other improvements and simplifications might also be made. For instance, rather than put the burden on the tag or seal of verifying that the TLI has not been moved since its line was revealed and its putative location established, a special device could be available where warheads are stored, which could be put in place within minutes of query; it would rest an arm on the TLI and would be equipped with sealed sensors to show that neither this instrument nor the TLI had been moved or emplaced after the time of query.
But very few rational and knowledgeable decision makers were willing to consider exchanging the totality of identity and location information on all of their warheads. They could just not get past the thought that somehow these tables in the possession of the adversary might reveal their secrets. Accordingly, in the 1990 paper I referred to a scheme in which so much of the information is deleted that there is no secret to be revealed. The encrypted line (which no longer needs to be encrypted) does not actually contain the information; it is too short to have the secret information. It serves only to validate the corresponding line in the table when it is ultimately revealed.
This approach sacrifices nothing compared with possessing the encrypted data itself. After all, the side that owns the TLI could always have refused a request to decrypt that specific line.
The key to validating these tables is the Secure Hash Standard.(5) This specifies a Secure Hash Algorithm, SHA-1, "for computing a condensed representation ("digest") of a message or a data file." (A secure "hash" is a smaller number of bits or characters derived from a message that depends upon every character of the message in such a way that "it is computationally infeasible to find a message which corresponds to a given message digest, or to find two different messages which produce the same message digest."
The SHA-1 produces a 160-bit message digest from any message or file of length less than 2 to the 64th power. Since this corresponds to 10 to the 19th power and the text of a normal novel is on the order of 10 to the 7th bits, SHA-1 is perfectly adequate to provide a digest of any of the messages that concern us here.
The Secure Hash Algorithm is entirely public and has been reviewed extensively for its cryptographic adequacy. There is surely no way in which the TLI's owner could worry about revealing information by providing the message digest.
The exchange of message digests can begin before there is any agreement actually to provide information. But the message digest can be very useful at the same time to the owning country in its TLI protection, control, and accounting of these objects. Of course, when the actual line corresponding to a TLI is provided in response to a query, or in response to the inspection of the TLI, the inspecting party simply uses SHA-1 to transform what is supposed to be the real information, and determines whether the message digest so produced is the digest that has been provided in the table.
ENTRY INTO THE VERIFICATION REGIME
A warhead or an amount of SNM in a container could be entered into the verification regime by affixing a simple tag and noting the type and sub-type of warhead, etc. It might also be necessary to note the type of container and the orientation of the warhead within the container. Deployed warheads, or warheads that are taken from containers and that become deployed, might have a tag affixed in an approved fashion and could also have a seal (such as the fiber optic purse of the referenced documents) to provide assurance that the tag still refers to the same warhead. At some later time, the system might acquire detailed information for validating the identity.
To be specific, assume that a number of containers assert that their contents is a W-88 warhead in a Mk-5 reentry vehicle. Two approaches are discussed for verifying that a TLI contains the warhead as stated. One of those is the measurement of "attributes", which might include at least a minimum mass of SNM, etc. I believe that the attributes are, perforce, so inaccurate that they do not provide reasonable verification or even transparency. For instance, if some warheads have as little as 4 kg of Pu, whereas others have 6 kg, the attribute for Pu would have to be set well below 4 kg, in order not to have too many rejections of those low-Pu warheads. A 6-kg primary could be converted into a 4-kg warhead (if that were possible) and 2-kg of Pu sold. To the extent that an attribute system depends upon tags and seals, further measurement of attributes can be dispensed with, because they add little, in the case of nuclear warheads.
Considerably more confidence can be placed in a Passport (Russian term) or Template (American term) approach which makes use of detailed and precise measurements of radiation characteristics of the TLI. The data obtained are sufficiently detailed so that they would provide useful weapon design information. While the U.S. and Russia might ultimately be willing to exchange such information, to release it into an international system would foment nuclear weapon proliferation rather than inhibit it. So the idea is to have precision measurement combined with an information barrier. For instance, in 1989 Brookhaven National Laboratory demonstrated the Controlled Intrusiveness Verification Technology (CIVET) approach, using computers without persistent memories to make decisions without the release of sensitive data. This was demonstrated to Russian personnel in 1997 at Oak Ridge in preparation for the Mayak storage facility. Similar systems have been demonstrated at Sandia National Laboratory and at the Pantex facility. Recent measurements taken with Sandia's Trusted Radiation Inspection System (TRIS) show the power of the (template) system in discriminating among 15 objects (8 pits, 5 fully functional bombs or reentry vehicles, and 2 secondaries).
Fig. 1 indicates the gamma ray spectrum of plutonium. The various lines can be used to help distinguish (in attribute or template fashion) so-called weapon plutonium from civil plutonium, although that distinction is not important in the weapon usability of plutonium. Nevertheless, it could prevent the substitution of civil plutonium for something that claims to have come from a nuclear weapon.
The energy region 635 to 665 keV is expanded in the lower right of the curve.
Fig. 2 is a simple illustration of the external observation via neutron counting of a sphere and a flat disk of plutonium. The two can readily be distinguished.
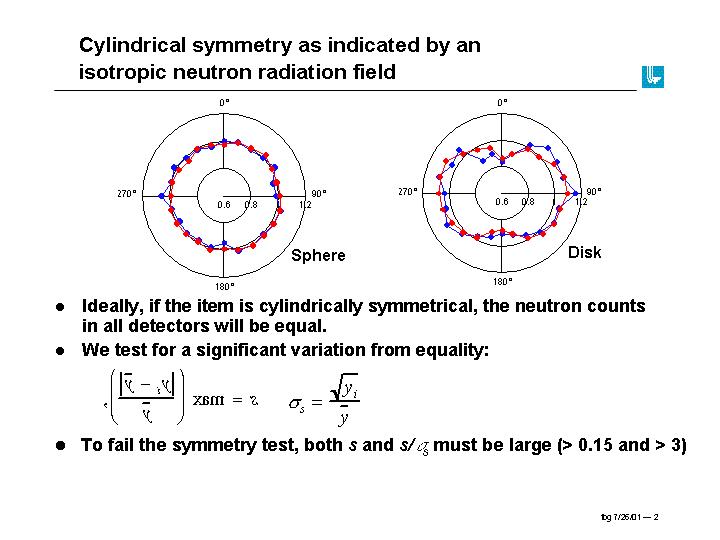
Fig. 3 shows the regions used in a template approach with a high-resolution germanium detector in order to verify that a given item claiming to be one or another nuclear device is what it claims to be.
Fig. 3 - Energy group structure used to analyze low-resolution spectral data
| Energy Range (keV) |
Principal Significance of the Energy Group |
Template Uncertainty (%) |
| 80 - 120 | U and Pu x-rays | 10 |
| 120 - 160 | continuum | 1 |
| 160 - 172 | sensitivity to energy-calibration error | exclude |
| 172 - 198 | 235U at 186 keV | 1 |
| 198 - 230 | 237U at 208 keV, variable in plutonium | exclude |
| 230 - 290 | continuum | 1 |
| 290 - 350 plus 390 - 500 |
239Pu full-energy peak region (change in sum of counts is insensitive to energy calibration error) | 1 |
| 350 - 390 | 239Pu full-energy peak region | 1 |
| 500 - 600 | continuum | 10 |
| 600 - 711 | 241Am at 662 keV, variable in plutonium | 20 |
| 711 - 821 | 238U at 766 keV | 2 |
| 821 - 936 | continuum | 20 |
| 936 - 1090 | 238U at 1001 keV | 1 |
| 1090 - 1200 | continuum | 5 |
| 1200 - 2480 | continuum from 238U and 232U | 20 |
| 2480 - 2750 | 232U at 2614 keV, variable in HEU | 30 |
In Fig. 4, the templates are arrayed in the first row, with "Px" one of eight pits; the five "Fx" fully functional bombs of different types; and the two "Sx" being two secondaries in their canisters.
Fig. 4 - Average  m2 for Comparisons of Measurements with Empirical Templates
m2 for Comparisons of Measurements with Empirical Templates
| Template | |||||||||||||||||
| Source | # | Back | PA | PA* | PB | PC | PD | PE | PF | PG | FB | FC | FD | FE | FF | SB | SF |
| PA | 1 | 1285 | .6 | 30 | 86 | 102 | 98 | 89 | 140 | 98 | 1039 | 75 | 414 | 680 | 782 | 5223 | 789 |
| PA | 2 | 1247 | 1.7 | 26 | 78 | 101 | 96 | 86 | 136 | 97 | 940 | 69 | 378 | 635 | 766 | 4565 | 765 |
| PA | 3 | 1298 | 1.3 | 31 | 85 | 97 | 92 | 86 | 141 | 92 | 1057 | 75 | 436 | 702 | 814 | 5056 | 817 |
| PA | 4 | 1320 | .9 | 34 | 93 | 105 | 100 | 92 | 143 | 100 | 1123 | 84 | 457 | 728 | 817 | 5544 | 827 |
| PA* | 1 | 1034 | 47 | .7 | 61 | 120 | 118 | 83 | 130 | 111 | 572 | 25 | 180 | 394 | 560 | 3391 | 547 |
| PA* | 2 | 1021 | 42 | 1.1 | 60 | 122 | 119 | 83 | 124 | 112 | 550 | 29 | 169 | 375 | 536 | 3417 | 524 |
| PA* | 3 | 1030 | 43 | .9 | 65 | 120 | 118 | 87 | 135 | 111 | 569 | 25 | 171 | 379 | 533 | 3594 | 524 |
| PB | 1 | 1009 | 121 | 107 | 1.2 | 93 | 91 | 15 | 27 | 81 | 558 | 91 | 319 | 547 | 794 | 1380 | 760 |
| PB | 2 | 1008 | 117 | 101 | 1.0 | 95 | 93 | 14 | 25 | 84 | 548 | 86 | 304 | 528 | 771 | 1427 | 740 |
| PB | 3 | 1000 | 119 | 103 | 1.0 | 95 | 93 | 14 | 25 | 83 | 542 | 88 | 305 | 526 | 770 | 1364 | 739 |
| PB | 4 | 996 | 117 | 101 | .9 | 95 | 93 | 15 | 25 | 83 | 541 | 89 | 305 | 528 | 772 | 1361 | 740 |
| PC | 1 | 2023 | 497 | 740 | 698 | .7 | 1.0 | 263 | 398 | 7.8 | 2126 | 808 | 1777 | 1762 | 1860 | 4010 | 1846 |
| PD | 1 | 2016 | 496 | 733 | 681 | 1.2 | .8 | 253 | 385 | 5.8 | 2112 | 794 | 1763 | 1755 | 1857 | 3985 | 1842 |
| PE | 1 | 1328 | 179 | 195 | 32 | 84 | 82 | .8 | 25 | 70 | 923 | 177 | 605 | 863 | 1108 | 1994 | 1081 |
| PF | 1 | 1284 | 172 | 190 | 36 | 128 | 124 | 20 | .7 | 112 | 858 | 203 | 566 | 821 | 1071 | 1836 | 1045 |
| PG | 1 | 2003 | 492 | 710 | 623 | 9.0 | 6.8 | 221 | 342 | .5 | 1982 | 761 | 1665 | 1719 | 1862 | 3527 | 1843 |
| FB | 1 | 317 | 129 | 84 | 116 | 156 | 156 | 131 | 139 | 152 | .8 | 92 | 32 | 7.7 | 42 | 400 | 27 |
| FB | 2 | 312 | 129 | 82 | 113 | 154 | 153 | 128 | 137 | 150 | .9 | 90 | 31 | 8.2 | 45 | 381 | 29 |
| FB | 3 | 312 | 123 | 83 | 113 | 152 | 151 | 128 | 135 | 149 | .8 | 91 | 32 | 8.5 | 45 | 386 | 29 |
| FC | 1 | 973 | 110 | 29 | 84 | 123 | 124 | 99 | 181 | 115 | 496 | .8 | 140 | 336 | 491 | 3102 | 480 |
| FD | 1 | 540 | 113 | 51 | 90 | 139 | 139 | 111 | 142 | 134 | 63 | 43 | .9 | 34 | 128 | 1217 | 113 |
| FE | 1 | 557 | 157 | 99 | 145 | 189 | 188 | 161 | 183 | 184 | 11 | 102 | 26 | .6 | 46 | 790 | 33 |
| FF | 1 | 511 | 211 | 154 | 205 | 260 | 257 | 223 | 227 | 254 | 55 | 174 | 86 | 31 | 1.0 | 1477 | 6 |
| SB | 1 | 123 | 134 | 112 | 125 | 142 | 141 | 130 | 130 | 140 | 52 | 118 | 88 | 64 | 66 | .8 | 57 |
| SB | 2 | 118 | 136 | 113 | 125 | 142 | 142 | 130 | 130 | 140 | 54 | 118 | 89 | 66 | 66 | 1.3 | 58 |
| SB | 3 | 130 | 135 | 114 | 128 | 144 | 143 | 133 | 134 | 142 | 53 | 120 | 90 | 65 | 65 | .8 | 57 |
| SB | 4 | 121 | 135 | 113 | 126 | 143 | 142 | 131 | 131 | 141 | 54 | 119 | 90 | 66 | 66 | 1.5 | 58 |
| SF | 1 | 414 | 189 | 139 | 181 | 229 | 227 | 197 | 199 | 225 | 27 | 156 | 77 | 22 | 6.4 | 861 | .5 |
* Pit A inside a shipping container (all other pits are in AL-R8 containers).
The first column indicates the actual source presented to the counting system. All templates and sources were in a standard "AL-R8" container, while PA* was inside a shipping container instead.
The "goodness of fit" of the measurement vs. the templates is shown in the cells of the illustration. A goodness of fit below 2 is never seen except when a particular source is compared with the proper template, with the exception of PC and PD. These two pits are almost identical and hence are indistinguishable by this technique.
Since a template measurement system with an information barrier (TMS/IB) might simply illuminate a red light if the claimed TLI was not one of the claimed class, and a green light if it was, no secret information could be legitimately obtained in the process. However, the inspected party would want to make sure that detailed clandestine measurements were not being taken, and for this reason the measuring instrument is always assumed to remain with the inspected party.
However, the inspecting party has much greater concern: First, that the green light does not automatically come on after a "counting interval" whatever the content of the container. Second, if the TMS/IB is truly making measurements of the claimed TLI, then how can one be sure that the template has not been changed to accord with what the TLI actually is?
The approach is one of joint preparation of templates in a "trusted system" which is fully understood by both sides and perhaps chosen among several available for the task. The result is a template prepared either from a "golden warhead" (in analogy to the "golden chip" for automated inspection of semiconductor products), or as an average of several warheads claimed to be identical and measured by the TMS/IB in a cooperative fashion to be similar in characteristics.
Again, the Secure Hash Algorithm SHA-1 comes into play in assuring the inspecting party that the template that remains in possession of the inspected party has not changed.
Much more can be said about such measurements and their supplementation by heat, container weight, and the like. Similarly, a lot can be said about tags and seals, but this is no place for an exhaustive presentation.
WARHEAD DISMANTLEMENT
In the work done in the United States and presumably in Russia and Britain on warhead dismantlement, there is also the tension between assurance that a warhead has indeed been dismantled and the SNM properly conserved and entered into the appropriate materials protection, control, and accounting (MPCA) system, on the one hand, and the preservation of nuclear secrets against proliferation or the improvement of nuclear stockpiles. In the late 1960s, the Arms Control and Disarmament Agency, Atomic Energy Commission, and Department of Defense carried out experiments on verifiability of warhead dismantlement under the title Project Cloud Gap. Some 40 warheads undergoing scheduled disassembly were monitored, together with 32 objects that were not warheads. Since the inspectors were cleared U.S. personnel, no effort was made to hide classified information, although the report suggested that such information could be concealed.
An approach to dismantling warheads is clear-- use a chain of custody for the warhead in its container or otherwise bearing its tag and appropriate seal to the portal of a relatively small and fully inspectable building where dismantling is to take place. In the building, the warheads will be dismantled and their SNM, itself, placed into the MPC&A transparency system.
In principle, then, there will be a steady stream of warheads coming in, and tagged and sealed SNM coming out. The inspectors' concern is that material might be accumulated inside the facility for later use in making more efficient warheads, or for sale or to be hidden. Another concern is that SNM (or undismantled warheads) would emerge and unbalance the residual forces. Coming out of the dismantling facility would be workers, equipment, safeguarded SNM, high explosives, and non-SNM residue from dismantling. Some of this might be valuable, and presumably an agreement would state whether it is to be crushed and rendered useless except as scrap, or whether it is permitted to be retained for whatever use might be made of it.
Thresholds would need to be set for monitoring the streams that are not SNM to set a limit on the amount of SNM that might escape in this way.
Periodically, work in the facility should stop with all SNM either in the form of warheads still bearing their tags or seals, or having been transferred to its container with tag and seal. A visiting team would then inspect the facility, which should be constructed in such a fashion that SNM could not be secretly accumulated. Inspectors would have free rein to use radiation detection equipment, since there would be no warheads or SNM to be found, except a relatively few that could be moved from a room where they might be stored to a room that had already been "swept" and found clean of SNM. This would enable the first room to be swept as well.
Arguments are heard that existing dismantlement facilities are used also for the assembly or remanufacture of nuclear warheads, and so would be unsuitable or very costly to submit to inspection in this way. Indeed, the larger the facility, the more time and effort lost in an inspection. Facilities for manufacturing might need considerably more precise and more revealing jigs and fixtures than a disassembly system; and existing facilities might have all kinds of ventilation ducts, passages, and the like, that would need to be sealed or safeguarded in an inspection regime.
It seems preferable to build a minimal new facility rather than incurring the delay and uncertainty and cost of dealing with an existing one.
EXPEDITIOUS DISABLING OF WARHEADS
Most nuclear warheads contain some power source such as a lithium battery or a "thermal battery". Many contain reservoirs for tritium and deuterium, for boosting the fission reactions.
Under some circumstances, such components can readily be removed in the field, because they may have limited life and are arranged for such exchange. But a warhead could be restored to health simply by replacing the missing element.
A more permanent method, pit stuffing, for disabling a nuclear warhead was introduced in this context by Matthew Bunn,(6) and I commented in the same issue of the FAS Public Interest Report.(7)
To summarize, U.S. nuclear weapons could be disabled in this way because they are "hollow-boosted plutonium primaries" that consist of a hollow thin shell of plutonium inside an inert metal shell, the whole thing surrounded by high explosive. A small "fill tube" allows boost gas consisting of deuterium and tritium to enter the pit shortly before the weapon is fired. The weapon can be disabled and prevented from giving any nuclear yield (not just prevented from boosting) by filling the pit with bits of metal wire that are deformed in such a way that they cannot be removed via the fill tube. If the high explosive system were detonated, the inward moving plutonium would encounter the metal fill, and would never become critical. While this will work for U.S. weapons, it needs to be calculated by Russian experts for their own nuclear weapons, which may have a different structure.
In my comment on Matt Bunn's proposal, I note also that the work involved in pit stuffing needs to be addressed, that the degree of irreversibility needs to be established, and that verification is important.
And I suggest a couple of approaches to show that the pit really is full of wire, for instance by incorporating some microcuries of Co-60 in the stuffing wire. One set of gamma ray counters collimated to look at the pit from one side would thus give some counts in coincidence with another gamma ray telescope looking in a perpendicular direction, because Co-60 gives two simultaneous high-energy gamma rays. This could not be mimicked by gamma-ray sources that are not in the interior of the pit.
One would need to be sure that the only Co-60 present was in the stuffing wire. Else one could insert a tiny amount of Co-60 into the pit without sufficient inert material to do the disabling.
Because pit stuffing depends on some details of warhead design and fabrication, it is not an approach that can be prescribed blindly.
SUMMARY
Appropriate tags and seals can help solve the problem of verifying undertakings in regard to warheads, warhead dismantlement, and stocks of special nuclear materials.
The use of a Secure Hash Algorithm would enable information in each treaty limited item (TLI)-- identity and location-- to be stored in tables and a digest given to the other side or to the international community without any possibility of revealing secret information. At a later time, the appropriate line could be revealed and established with certainty by using the SHA to provide a digest that should match the secure hash that had been deposited previously
Warhead dismantling should take place in facilities specially built to be inspectable in such a fashion that occasional visits will establish that no special nuclear material has been diverted or retained.
Finally, disabling of warheads would benefit from more thought and ingenuity, so that irreversible reductions can be obtained without waiting for dismantling of the agreed weapons.
** Four figures go here **Encl:
08/01/88 "Tags and Seals for Arms Control Verification,"
by R.L. Garwin (Draft 1) for the Bulletin of The
Council for Arms Control, LONDON. (080188TASV)
RLG:jah:1187TVWS:070601TVWS
----------------
- "Confidence, Security & Verification-- The challenge of global nuclear weapons arms control," Atomic Weapons Establishment, Aldermaston, AWE/TR/2000/001. Also at http://www.awe.co.uk
- "Societal Verification," by J. Rotblat, Chapter 6 in the Pugwash book A Nuclear-Weapon-Free World: Desirable? Feasible? edited by J. Rotblat, J. Steinberger, and B. Udgaonkar, Westview Press, 1993, pp. 103-118.
- "Verification of Limits on Conventional Forces in Europe (CFE)," by R.L. Garwin presented March 15, 1990. Talking paper for meeting of CISAC with group from the Royal Society, London, ENGLAND.
- "Tags and Seals for Verification," by R.L. Garwin published in Bulletin of The Council for Arms Control, LONDON, October 1988. (The attached paper was edited for publication).
- Federal Information Processing Standards Publication 180-1 (FIPS 180-1)
- "'Pit-Stuffing': How to Disable Thousands of Warheads and Easily Verify Their Dismantlement," by M. Bunn, F.A.S. Public Interest Report, Vol. 51, No. 2, March/April 1998.
- "Comment on Matt Bunn's 'Pit Stuffing' Proposal," by R.L. Garwin, F.A.S. Public Interest Report, Vol. 51, No. 2, March/April 1998.
*******************************************************************
TAGS AND SEALS FOR ARMS CONTROL VERIFICATION
by
Richard L. Garwin
IBM Research Division
Thomas J. Watson Research Center
P.O. Box 218
Yorktown Heights, NY 10598
(914) 945-2555
(also
Adjunct Professor of Physics,
Columbia University;
Adjunct Research Fellow,
CENTER FOR SCIENCE AND INTERNATIONAL AFFAIRS
Kennedy School of Government
Harvard University)
August 1, 1988
DRAFT for the
Bulletin
of
The Council for Arms Control
LONDON
214>TASV 080188TASV DRAFT 1 08/01/88
Views of the author, not of his organizations
For centuries, military forces of other nations or alliances have provoked the specter of attack on ourselves or on our allies. In recent decades, as for much of history, a principal means of dealing with these fears and threats has been the maintenance of military forces of our own-- in some cases to serve literally as a shield against weapons, in some cases as a means to destroy the forces of the other side in combat, and (especially to counter nuclear weapons that each could destroy a major city) to pose a threat of such destruction to the other side as to deter major attack on our side.
Arms control in the form of explicit treaties can limit the military capability or readiness on the other side, as an alternative or supplement to military capabilities on our side. A concrete example is the U.S.-Soviet INF Treaty of December 1987 eliminating land-based cruise missiles or ballistic missiles (nuclear or non-nuclear, of range between 500 km and 5500 km) from the armories of the two sides, wherever based, anywhere in the world. Three years hence, observation of a Pershing 2 or an SS-20 missile anywhere in the world will establish a violation of the INF Treaty, and a major verification establishment has been created by the U.S., funded at some $200 M annually, to ensure detection of any significant Soviet violation of this treaty.
Looking toward the establishment of a possible START (Strategic Arms Reduction Treaty) regime to realize the 50% reduction in long-range nuclear weapons agreed in principle by President Reagan and General Secretary Gorbachev December 1987, Soviet compliance will have to be verified (that is, non-compliance detected) without the lever of total elimination of the weapons involved. ICBMs will still be deployed and test fired; submarines with their ballistic missiles and multiple warheads will continue to operate, as will heavy bombers with their bombs and ALCMs. How are we to establish that the Soviet Union is not showing the other side of the coin of the notorious performance in which the same bombers were repeatedly flown over Red Square to inflate Western estimates of Soviet airpower? One can't require the other side to immobilize and expose to view all at one time every one of their ICBMs!
Furthermore, responsible, experienced former officials are concerned that 50% reductions will reduce U.S. submarines, missiles, and bombers and therefore reduce strategic stability, in that the fewer U.S. systems could more readily be destroyed by Soviet weapons and thus prevent a U.S. nuclear response.
Conversely, reducing the number of multiple, independently targeted reentry vehicles (MIRVs) on each U.S. ICBM or SLBM would assuredly improve survivability above its present value, but how can one verify that weapons removed and destroyed are not replaced?
Both the verification of numerical limits on launchers, and the assurance of reduced MIRV deployment can be aided by a technique so common in everyday life that we pay little attention. That is the use of tags to identify each of the authorized launchers (ICBM, SLBM or heavy bomber, perhaps) and a seal to ensure each tag has remained at all times associated with the particular item it legitimizes.
For instance, authorized taxicabs in New York City are painted yellow. At present, the market worth of permission to operate a taxi is about $100,000; a metal "medallion" riveted to the hood of the yellow vehicle carries an identifying number to allow ready verification that a yellow vehicle is indeed one of the numerically limited, legitimate "yellow cabs."
If a tag can be made impossible to counterfeit (even with means available to national intelligence services), and a seal provided that ensures that the tag will be cancelled if removed from the item it legitimizes, the degree of cooperation established in the INF Treaty would then allow verification of numerical limits with confidence similar to that for elimination of the weapons.
In that case, the observation of even a single untagged weapon would be a violation; a numerical limit is in this way equivalent to a ban on untagged weapons.
It is reported that the Defense Science Board of the U.S. Department of Defense has recommended a set of physically unique tags of special adhesive tape incorporating mica fragments to play the role of both seal and tag on appropriate treaty-limited items. Applied to the single assembly joint on the canister of a sea-launched cruise missile, for example, such a tag would prevent the unobserved removal of the nuclear warhead for other purposes and its absence would reveal (like the Yellow Cab medallion) that a similar untagged canister was illegitimate. In analogy to a fingerprint, the "glint-tag" applied to a limited Soviet item would have a unique pattern recorded by camera when illuminated by light at a particular position known to the U.S. verification establishment.
I personally prefer an electronic microchip tag of very great applicability, better adapted to remote readout than is the tag that depends on physical uniqueness-- "glint tag," banknote, police badge or medallion.
The microchip tag in its housing might be the size of my digital wristwatch. Like the watch, it would be powered by a lithium battery, but it would have two-- for redundancy and to allow one to be replaced without losing power on the chip. All verification tags on both sides would be physically identical and made to specifications openly shared between the two sides. Each side might want to dissect a considerable number of chips to verify that they are identical and that they do not contain explosives, covert radio transmitters, etc.
The proper function of such a tag would be achieved by loading it at the factory with two lists of 100 random numbers, each 8 digits (bytes) long. In principle, the U.S. would load twice as many chips as are required by the Soviet items to be limited, and for each chip to be attached to an army tank, ICBM, or other limited item, would keep an identical chip loaded in parallel with the same numbers. Retaining a list of serial numbers of the twinned chips would allow one to refer to the retained twin to determine the proper response of the deployed chip.
Loading the chip would be done after inserting the batteries, by an interface similar to the infrared remote control for your TV set. After 100 number pairs were loaded, the chip would switch automatically to another mode in which it would remain so long as the power was applied. In this verification mode, the chip would respond with the next number in the second list when queried with the corresponding number in the first list. No chip would respond again within one hour of a previous inquiry, to prevent inadvertent exhaustion of the chip.
(Other approaches that might be used would incorporate an encryption feature on the chip. Each chip would then be loaded with its own encryption "key" retained by the opposing verification service. Such a system would allow unlimited numbers of inquiry. A "public key" cryptographic system would permit still other desirable features, but the simple "list" approach adequately describes the concept.)
The tag "response" would be available via a small infrared light-emitting diode ("LED") with which we are all familiar, providing reliable communications to an interface a few inches away without the possibility of coupling destructive signals into the chip, or of difficulties due to metal contacts of poor quality.
To ensure that the tag remains with the treaty-limited item it legitimizes, it is attached with a fiber-optic "seal" consisting of a plastic or glass optical fiber clad with a layer of plastic or glass to prevent the light from leaking out of the fiber if its surface is wet or dirty. An LED in the chip sends a very brief (billionth of a second) pulse of light into one end of the fiber inserted in the tag body (wristwatch size) 100 times each second, and a photodiode in the tag receives the light signal from the other end of the fiber (also inserted in the tag body) and is used to measure very precisely the signal delay and its intensity. On a standard pulse like this, it is easy to measure the delay time to 10 trillionths of a second-- the time it takes light to travel 2 millimeters in the fiber. If the tag is attached to a tank turret by the fiberoptic seal looped through a hole in the massive turret, it could not be removed without interrupting the infrared monitoring of seal continuity.
Such interruption, by design, would erase the number list in the chip, which would no longer provide authentication or legitimization. The tag would be built with apertures for two fiberoptic loops, in series. In the tank-turret example, one pair of apertures could be permanently occupied by a short dummy loop. A more interesting and generally useful case involves a fiberoptic "string bag" such as is used (in ordinary string form) in Europe for carrying items home from the grocery. Such purses might be available in various sizes, prepared from fiberoptic material knitted in such a way that the gross mesh of the bag might be a couple of inches (5 cm) across. The joints must be welded in such a way that they could not be separated without breaking the fiber or interfering with the light signal passing through the fiber. The purse apertures could readily accommodate mounting bolts for the cruise missile, nuclear warhead, or whatever item is being tagged, without being large enough to allow the removal of the item, nuclear material, etc. After the purse is applied to enclose the item (cruise missile canister, for example), the open end of the purse might be closed by threading a second fiber optic loop a few inches long to close the end of the purse and to engage both second-loop apertures in the tag. Once applied in this way to contain the canister in the purse and to close the purse with the loop, the tag will continue to be available to certify the legitimacy of the tagged item.
To verify a numerical limit, it is necessary to request the other side to provide the tag number and to query the tag of a treaty-limited item observed by inspection or intelligence. In concept, one side's verification establishment might send an individual to visit the identified item which would be frozen in position until the visit would take place. If there are N legitimate items and M clandestine, so that there is a fraction F = M/(N+M) of clandestine items, there would be 90% confidence in finding one or more untagged items in about 2.3/F inspections at random (some 23 inspections if the surplus F is to be limited to 10% or less).
More generally, if there is a fraction F of clandestine items in the category limited, and one wants to have confidence C that at least one clandestine item will be found, then one might sample S individual items to determine compliance. On the assumption that every one of the items (legitimate and illegitimate) is equally accessible to the sampling system, the probability of finding an illegitimate (untagged) item in a single sample is F. The probability that no violation will be found in a single sample is then (1-F). The probability that no violation will be found in S samples is (1-F) multiplied by itself a total of S times, and this is the probability that the other side could escape detection if indeed they had an excess fraction exactly F. Thus, this is the complement of the confidence C that the verifier would have in finding a violation, and this quantity is equal to (1-C). One can solve this equation for the required number of samples S to achieve the required confidence C, with the answer
S = (log (1 - C)) / (log (1 - F))
Because the item and its environment would have to be immobilized ("frozen") until the verification visit was complete, there is a saving of cost both to the inspecting side and the side inspected if verification can be accomplished remotely. This might be accomplished (without any possibility of using the tag as a "beacon" for attack on the items) by a cooperative communication system using communication relays specially provided to both sides. Such a relay box would have an infrared communication link to the tag from a distance of a few inches, and would communicate with a standard military or civilian communications satellite. Imagine first the example of a large mobile missile.
In a routine inquiry, the Soviets might be asked to identify the precise locations of any missiles within a small region in which our unilateral intelligence indicates (has photographed, for instance) a missile. If among the ones indicated there is none corresponding to the observed position, the missiles in the area are frozen and a visit is made to a number of them, including the discovery of the unadmitted one. If it has been dragged away by the time we visit, a violation would be charged; the situation is exactly the same as with the detection of a missile under a total ban. If the observed missile is one of those listed by the Soviets, we might choose to verify the missile at 57.753 N, 75.147 E by asking the Soviets to bring one of the verification relays to the missile. They would have, say, 2 hours to do this, after which we would send a numerical inquiry via satellite, receiving the reply with the speed of light. Multiple satellite receivers could detect the relay transmission and pinpoint its location to accuracy available with the new global positioning system GPS-- some 15 meters or so. If the transmission provides the proper number from the list in the chip queried, the chip in question is still attached to its limited item. And the verification team has replaced a visit at some hundreds or thousands of km distance by the analogue of a long-distance telephone call.
How do we know that the observed item is the one with the claimed tag, and that the Soviets have not communicated with the actual limited item 100 km away, relaying the response through the cooperative relay? The relay is observed by time-difference of arrival of the radio signal to be at the place desired to within 15 meters or so, and the radio signal could not have been diverted from the relay by a like distance without revealing that in the overall round-trip time of the radio signal. Can the tag chip do its processing in the requisite time of a few nanoseconds (billionths of a second)? It does not need to do so, because we can build a time delay into each chip, of precisely 100 nanoseconds, masking the delay of the tag chip without allowing masquerade by a real chip at any appreciable distance.
Naturally, personnel will visit occasionally to verify that some fiendishly clever scheme has not been widely used to separate tags from the limited items.
Should one want to verify de-MIRVing of ICBMs, SLBMs, or the reduction of the capacity of the rotary launcher of ALCM in the B-52, one can use such tags and seals to ensure that aluminum or concrete blocks are in place in the individual MIRV sockets on the post-boost vehicle (PBV) or rotary launcher. In this way one can be sure that at any time the claimed de-MIRVing is still fact.
The fiberoptic purse as seal can be made fragile enough that it does not interfere with the launching of a missile or the operation of the equipment in wartime, although the tag will of course be void.
Tags and seals have great promise in verifying compliance with agreements to limit weapons. The sea-launched cruise missiles (SLCM) pose a particularly severe problem because they are as yet limited by no agreement at all. My own preference is to ban all nuclear-armed SLCMs, but such a proposal is complicated and far reaching and goes beyond the space available here.
